Do You Need Penetration Testing for SOC 2 Compliance?
Understand whether pentesting is required for compliance and how to make the right security investment for your company.
.jpg)
If you're pursuing SOC 2 compliance, you've probably encountered conflicting information about penetration testing. Some vendors insist it's mandatory. Others treat it as an expensive add-on. Many founders discover unexpected pen testing costs only after months of working with their compliance platform.
Let’s clarify what you actually need to know about penetration testing and SOC 2, based on real experiences from startups going through this process.
What SOC 2 Actually Requires for Security Testing
SOC 2 Type 2 attestation doesn't explicitly mandate penetration testing. The framework requires you to demonstrate that you identify and address system vulnerabilities, but it doesn't prescribe specific testing methods.
However, this technical distinction often misleads founders. While you can theoretically achieve SOC 2 without pen testing, many auditors expect to see security testing as evidence of your vulnerability management controls. Without it, you'll need to provide alternative evidence, which can complicate your audit.
The SOC 2 framework is built off the AICPA’s Trust Services Criteria (TSC) which was published and revised in the 2017 AICPA Trust Services Criteria for Security, Availability, Processing Integrity, Confidentiality, and Privacy (with Revised Points of Focus – 2022) publication. There are 5 total TSC’s. Security is the only required criterion, implemented through the Common Criteria (dubbed “CC”) in the publication. The point in question around vulnerability assessment and penetration testing is CC7.1, of which the exact text is:
CC7.1
To meet its objectives, the entity uses detection and monitoring procedures to identify (1) changes to configurations that result in the introduction of new vulnerabilities, and (2) susceptibilities to newly discovered vulnerabilities.
Under CC 7.1, the fifth Point of Focus further discusses the requirement:
CC7.1 - POF 5 Conducts Vulnerability Scans
The entity conducts infrastructure and software vulnerability scans designed to identify potential vulnerabilities or misconfigurations on a periodic basis and after significant changes are made to the environment. Action is taken to remediate identified deficiencies in a timely manner to support the achievement of the entity’s objectives.
The only place the word “penetration test” is explicitly mentioned in the entire publication is in CC7.1 - POF 5:
CC7.1 - POF 5 Considers Different Types of Ongoing and Separate Evaluations
Management uses a variety of ongoing and separate risk and control evaluations to determine whether internal controls are present and functioning. Depending on the entity’s objectives, such risk and control evaluations may include first- and second-line monitoring and control testing, internal audit assessments, compliance assessments, resilience assessments, vulnerability scans, security assessment, penetration testing, and third-party assessments.
First, under SOC 2, an assessment of the Trust Services Criteria (what a SOC 2 audit is) does not require you to follow all Points of Focus, in fact the AICPA specifically states:
Some points of focus may not be suitable or relevant to the entity or to the engagement to be performed.
In such situations, management may customize a particular point of focus or identify and consider other characteristics based on the specific circumstances of the entity.
Further:
Use of the trust services criteria does not require an assessment of whether each point of focus is addressed.
Users are advised to consider the facts and circumstances of the entity and its environment in actual situations in relation to the entity’s objectives when evaluating the subject matter using the trust services criteria.
Notwithstanding all of that, the CC4.1-POF4 only lists penetration testing as a evaluation you may consider, and nothing further. SOC 2 is meant to be a very flexible framework that can be built around you and your risk landscape.
With that said however, your customers often care about security testing regardless of minimum compliance requirements. Enterprise security teams frequently request penetration testing reports during vendor evaluations. Companies without recent pen tests may face extended security reviews that can impact deal timelines.
The takeaway here is penetration testing isn't technically required for a valid SOC 2 report, and if your business doesn’t necessitate it or funds are tight - it can be pushed back until an enterprise requests it. It's often essential for the business outcomes you're trying to achieve through compliance.
Penetration Testing vs. Vulnerability Scanning
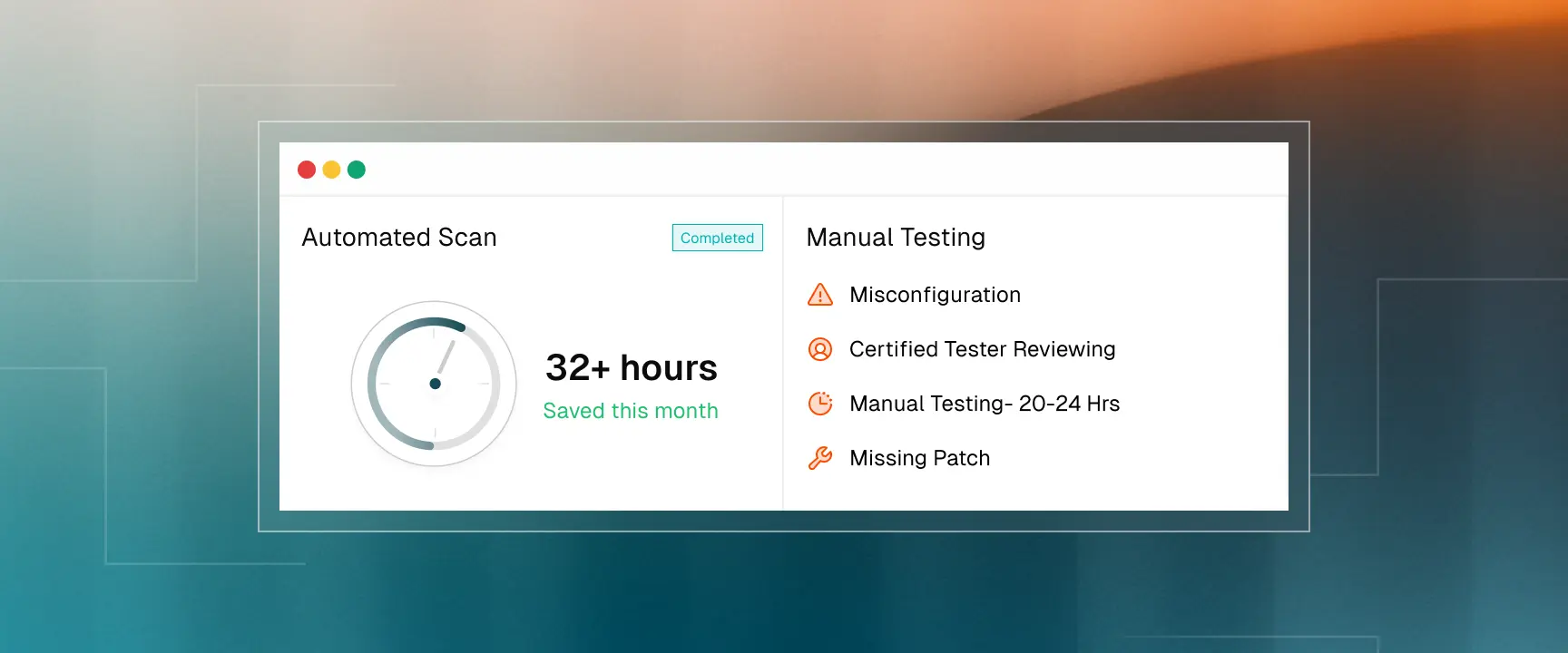
Many founders discover too late that their compliance platform's "security testing" is actually just automated vulnerability scanning. Understanding this distinction helps you evaluate what you're actually getting for your investment.
Vulnerability scanning uses automated tools to check for known security issues in your systems. These scans identify outdated software, missing patches, and common misconfigurations. The process typically takes hours and requires minimal human involvement. Common providers are Tenable, Qualys, OpenVAS, Aikido Security, and more.
Penetration testing involves certified security professionals manually attempting to compromise your systems using real attack techniques. Testers combine multiple vulnerabilities, test business logic, and explore attack paths that automated tools cannot detect. A penetration test for a typical SaaS application requires 20-25 hours of skilled human analysis for a small startup, and up to 100 for a larger companies.
The difference matters for both security and compliance. Automated scans catch surface-level issues but miss the complex vulnerabilities that lead to actual breaches. When enterprise customers request "penetration testing reports," they're looking for evidence of manual security testing, not automated scan results.
Some vendors blur this distinction in their pricing, offering "penetration testing" that's actually just vulnerability scanning with a manual review. You should clarify whether you're getting actual manual testing hours from certified professionals.
Why Enterprise Customers Care About Your Penetration Testing Reports
A common axiom is that compliance ≠ security. There are Minimum Compliance Requirements (MCR) and Discretionary Security Requirements (DSR) and ideally, your security program creates compliance as a by-product of it’s existence and enforcement. Penetration testing falls into the DSR side, but improves your security posture and compliance positioning.
Enterprise sales cycles often move faster when you can immediately provide comprehensive pen testing reports. Companies with recent pen tests may be able to skip extended security assessments.
The compound benefits become clear over time. Each pen test builds on previous findings, helping you develop stronger security practices. Your engineering team learns to anticipate security issues. Your security posture improves beyond mere compliance. This maturity shows in customer conversations and can accelerate future security reviews.
Consider penetration testing as product development for security. Just as you wouldn't launch features without testing, you shouldn't ingest sensitive data and set up controls without validating they actually work.
How to Choose the Right Penetration Testing Approach for Your Startup
Your approach to penetration testing should align with your business goals, customer requirements, and security maturity.
Start by understanding your customers' expectations. If you're selling to enterprises, regulated industries, or security-conscious markets, plan for comprehensive pen testing from the beginning. These customers often ask for recent reports and may expect regular testing. Building this into your compliance strategy prevents delays later.
Consider your internal capabilities. Small teams often benefit from integrated pen testing that includes remediation support. Larger teams with security expertise might prefer managing standalone tests. Your choice should reflect both current capabilities and growth plans.
Evaluate vendors based on transparency and alignment with your needs. Ask specific questions about testing methodology, tester certifications, hours included, and retest policies. Vendors who include comprehensive testing in base pricing often provide better overall value than those positioning it as an add-on.
Think beyond your first audit. If you plan to conduct regular testing as part of your security program, your initial decision impacts ongoing costs and operations. Platforms that integrate testing into their workflow reduce coordination overhead over time. This efficiency becomes valuable as your team grows and compliance requirements expand.
If you're pursuing SOC 2 compliance, you've probably encountered conflicting information about penetration testing. Some vendors insist it's mandatory. Others treat it as an expensive add-on. Many founders discover unexpected pen testing costs only after months of working with their compliance platform.
Let’s clarify what you actually need to know about penetration testing and SOC 2, based on real experiences from startups going through this process.
What SOC 2 Actually Requires for Security Testing
SOC 2 Type 2 attestation doesn't explicitly mandate penetration testing. The framework requires you to demonstrate that you identify and address system vulnerabilities, but it doesn't prescribe specific testing methods.
However, this technical distinction often misleads founders. While you can theoretically achieve SOC 2 without pen testing, many auditors expect to see security testing as evidence of your vulnerability management controls. Without it, you'll need to provide alternative evidence, which can complicate your audit.
The SOC 2 framework is built off the AICPA’s Trust Services Criteria (TSC) which was published and revised in the 2017 AICPA Trust Services Criteria for Security, Availability, Processing Integrity, Confidentiality, and Privacy (with Revised Points of Focus – 2022) publication. There are 5 total TSC’s. Security is the only required criterion, implemented through the Common Criteria (dubbed “CC”) in the publication. The point in question around vulnerability assessment and penetration testing is CC7.1, of which the exact text is:
CC7.1
To meet its objectives, the entity uses detection and monitoring procedures to identify (1) changes to configurations that result in the introduction of new vulnerabilities, and (2) susceptibilities to newly discovered vulnerabilities.
Under CC 7.1, the fifth Point of Focus further discusses the requirement:
CC7.1 - POF 5 Conducts Vulnerability Scans
The entity conducts infrastructure and software vulnerability scans designed to identify potential vulnerabilities or misconfigurations on a periodic basis and after significant changes are made to the environment. Action is taken to remediate identified deficiencies in a timely manner to support the achievement of the entity’s objectives.
The only place the word “penetration test” is explicitly mentioned in the entire publication is in CC7.1 - POF 5:
CC7.1 - POF 5 Considers Different Types of Ongoing and Separate Evaluations
Management uses a variety of ongoing and separate risk and control evaluations to determine whether internal controls are present and functioning. Depending on the entity’s objectives, such risk and control evaluations may include first- and second-line monitoring and control testing, internal audit assessments, compliance assessments, resilience assessments, vulnerability scans, security assessment, penetration testing, and third-party assessments.
First, under SOC 2, an assessment of the Trust Services Criteria (what a SOC 2 audit is) does not require you to follow all Points of Focus, in fact the AICPA specifically states:
Some points of focus may not be suitable or relevant to the entity or to the engagement to be performed.
In such situations, management may customize a particular point of focus or identify and consider other characteristics based on the specific circumstances of the entity.
Further:
Use of the trust services criteria does not require an assessment of whether each point of focus is addressed.
Users are advised to consider the facts and circumstances of the entity and its environment in actual situations in relation to the entity’s objectives when evaluating the subject matter using the trust services criteria.
Notwithstanding all of that, the CC4.1-POF4 only lists penetration testing as a evaluation you may consider, and nothing further. SOC 2 is meant to be a very flexible framework that can be built around you and your risk landscape.
With that said however, your customers often care about security testing regardless of minimum compliance requirements. Enterprise security teams frequently request penetration testing reports during vendor evaluations. Companies without recent pen tests may face extended security reviews that can impact deal timelines.
The takeaway here is penetration testing isn't technically required for a valid SOC 2 report, and if your business doesn’t necessitate it or funds are tight - it can be pushed back until an enterprise requests it. It's often essential for the business outcomes you're trying to achieve through compliance.
Penetration Testing vs. Vulnerability Scanning
Many founders discover too late that their compliance platform's "security testing" is actually just automated vulnerability scanning. Understanding this distinction helps you evaluate what you're actually getting for your investment.
Vulnerability scanning uses automated tools to check for known security issues in your systems. These scans identify outdated software, missing patches, and common misconfigurations. The process typically takes hours and requires minimal human involvement. Common providers are Tenable, Qualys, OpenVAS, Aikido Security, and more.
Penetration testing involves certified security professionals manually attempting to compromise your systems using real attack techniques. Testers combine multiple vulnerabilities, test business logic, and explore attack paths that automated tools cannot detect. A penetration test for a typical SaaS application requires 20-25 hours of skilled human analysis for a small startup, and up to 100 for a larger companies.
The difference matters for both security and compliance. Automated scans catch surface-level issues but miss the complex vulnerabilities that lead to actual breaches. When enterprise customers request "penetration testing reports," they're looking for evidence of manual security testing, not automated scan results.
Some vendors blur this distinction in their pricing, offering "penetration testing" that's actually just vulnerability scanning with a manual review. You should clarify whether you're getting actual manual testing hours from certified professionals.

Why Enterprise Customers Care About Your Penetration Testing Reports
A common axiom is that compliance ≠ security. There are Minimum Compliance Requirements (MCR) and Discretionary Security Requirements (DSR) and ideally, your security program creates compliance as a by-product of it’s existence and enforcement. Penetration testing falls into the DSR side, but improves your security posture and compliance positioning.
Enterprise sales cycles often move faster when you can immediately provide comprehensive pen testing reports. Companies with recent pen tests may be able to skip extended security assessments.
The compound benefits become clear over time. Each pen test builds on previous findings, helping you develop stronger security practices. Your engineering team learns to anticipate security issues. Your security posture improves beyond mere compliance. This maturity shows in customer conversations and can accelerate future security reviews.
Consider penetration testing as product development for security. Just as you wouldn't launch features without testing, you shouldn't ingest sensitive data and set up controls without validating they actually work.
How to Choose the Right Penetration Testing Approach for Your Startup
Your approach to penetration testing should align with your business goals, customer requirements, and security maturity.
Start by understanding your customers' expectations. If you're selling to enterprises, regulated industries, or security-conscious markets, plan for comprehensive pen testing from the beginning. These customers often ask for recent reports and may expect regular testing. Building this into your compliance strategy prevents delays later.
Consider your internal capabilities. Small teams often benefit from integrated pen testing that includes remediation support. Larger teams with security expertise might prefer managing standalone tests. Your choice should reflect both current capabilities and growth plans.
Evaluate vendors based on transparency and alignment with your needs. Ask specific questions about testing methodology, tester certifications, hours included, and retest policies. Vendors who include comprehensive testing in base pricing often provide better overall value than those positioning it as an add-on.
Think beyond your first audit. If you plan to conduct regular testing as part of your security program, your initial decision impacts ongoing costs and operations. Platforms that integrate testing into their workflow reduce coordination overhead over time. This efficiency becomes valuable as your team grows and compliance requirements expand.
21-year-old MIT dropouts raise $32M at $300M valuation led by Insight

Don't let manual compliance slow you down.





.webp)



.avif)










.webp)

