SOC 2 Audit Readiness: Playbook to Move Fast

Key Takeaways
- SOC 2 audit readiness requires documented security controls, clean cloud infrastructure configurations, approved policies, and continuous evidence collection across IAM, logging, change management, and access reviews, achievable in 4-6 weeks with AI automation versus 6-12 months manually.
- SOC 2 attests that your security controls meet the Trust Services Criteria required by enterprise procurement teams before signing contracts. With proper automation and AI-native tooling, founders can compress the traditional 6-12 month SOC 2 timeline into weeks, reducing engineering burden from 60-80 hours to under 15 hours while maintaining the control effectiveness auditors demand.
- Think of SOC 2 as a revenue problem, not a compliance checkbox. Every day without it costs you deals.
- "Audit ready" just means you have your controls documented, your cloud setup is clean, your policies are approved, and you can prove it all works.
- Focus on IAM, logging, change management, and access reviews. That's the 20% driving the other 80%.
- Most timeline delays come from back-and-forth with auditors, not the actual control work.
- This guide walks you through exactly what to do, how long it takes, and where things typically go wrong.
What Audit Readiness Means For SOC 2
The AICPA (the folks who created SOC 2) defines five areas they care about: Security, Availability, Processing Integrity, Confidentiality, and Privacy.
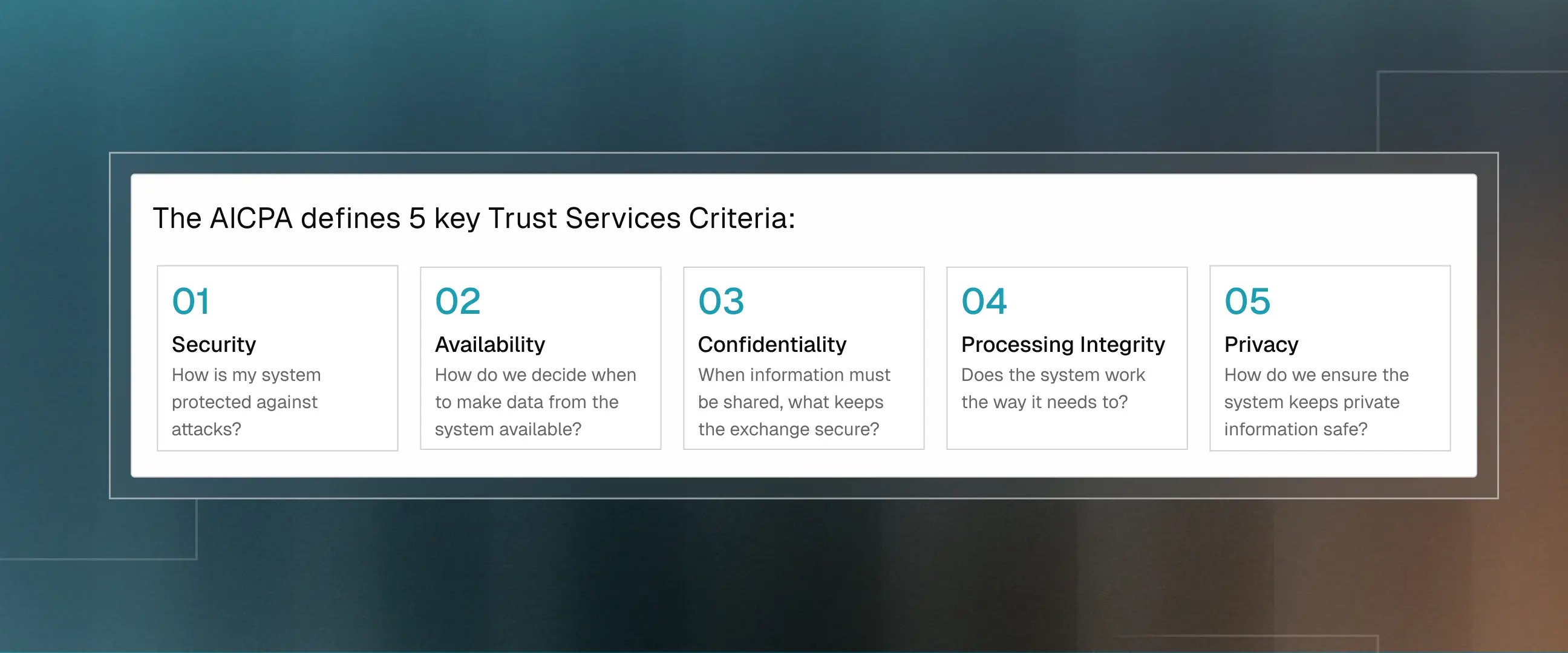
Security is the only mandatory Trust Services Criterion (TSC) for a SOC 2 audit. You do not have to include all five TSCs, but you cannot conduct a SOC 2 audit based solely on security if any of the other criteria apply to your service commitments. You must address all applicable TSCs.
Now, regardless of which criteria apply to you, being "audit-ready" means you have these fundamentals in place:
Being "audit ready" means you can show auditors five things.
- Your controls are mapped and working. You know what security measures you have, who owns them, and you can prove they're actually doing their job.
- Your cloud setup passes the tests. AWS recommends regularly cleaning up unused permissions and using their Access Analyzer tool. Basic stuff, but it trips up a lot of teams.
- Your policies are approved and signed. Leadership must formally approve your security policies, and your team must acknowledge them. Policies sitting in a Google Doc don't count.
- You've documented your system. Auditors need to understand what you've built: your infrastructure, how data flows, what third-party tools you use, and where the boundaries are.
You have evidence that things work. For Type II audits, you need logs and records showing your controls worked consistently over time. CISA recommends good logging because it provides a clear picture of what's happening and helps you catch issues fast.

SOC 2 Audit Readiness Checklist
Most SOC 2 guides make this way more complicated than it needs to be. Here's what auditors really care about:
- Identity & Access Management. Auditors want to see that you tightly control who can access your systems. At a high level, this means everyone using MFA, people only having the permissions they actually need, a simple process for adding and removing employees, and periodic reviews to confirm that access still makes sense. The NIST Cybersecurity Framework calls this a core protective function, and auditors agree.
- Logging & Monitoring. This is simply about ensuring your cloud environment keeps a record of what’s happening. NIST SP 800-53 outlines what you should log: password changes, failed logins, security setting changes, and admin actions. If something goes wrong, you need to be able to figure out what happened.
- Change Management. SOC 2 looks for basic discipline around how code gets into production. As long as changes go through review, your main branch is protected, deployments follow a predictable process, and your version control system tracks who did what, you’re covering what auditors care about most.
- Encryption. Encryption can sound intimidating, but SOC 2 only requires that data be encrypted at rest and in transit. You're using TLS 1.2 or higher. Keys are correctly managed. Nothing sensitive is sitting out in the open. Your cloud provider handles most of this by default, so it's usually just a matter of confirming it's turned on.
- Vulnerability Management. This is simply your rhythm for finding and fixing issues, running periodic scans, addressing critical findings within reasonable timelines, doing an annual pen test, and keeping systems patched. It demonstrates that you’re not ignoring security problems, which is all the audit is checking for. According to the Cloud Security Alliance, 39% of companies have already lost cloud data, and misconfiguration was the number one cause.
- Personnel Security. Finally, SOC 2 requires that your people follow basic security hygiene. Annual training, background checks where appropriate, simple onboarding and offboarding steps, and signed confidentiality agreements are enough to satisfy this category without any heavy lifting.
How Long Does SOC 2 Take?
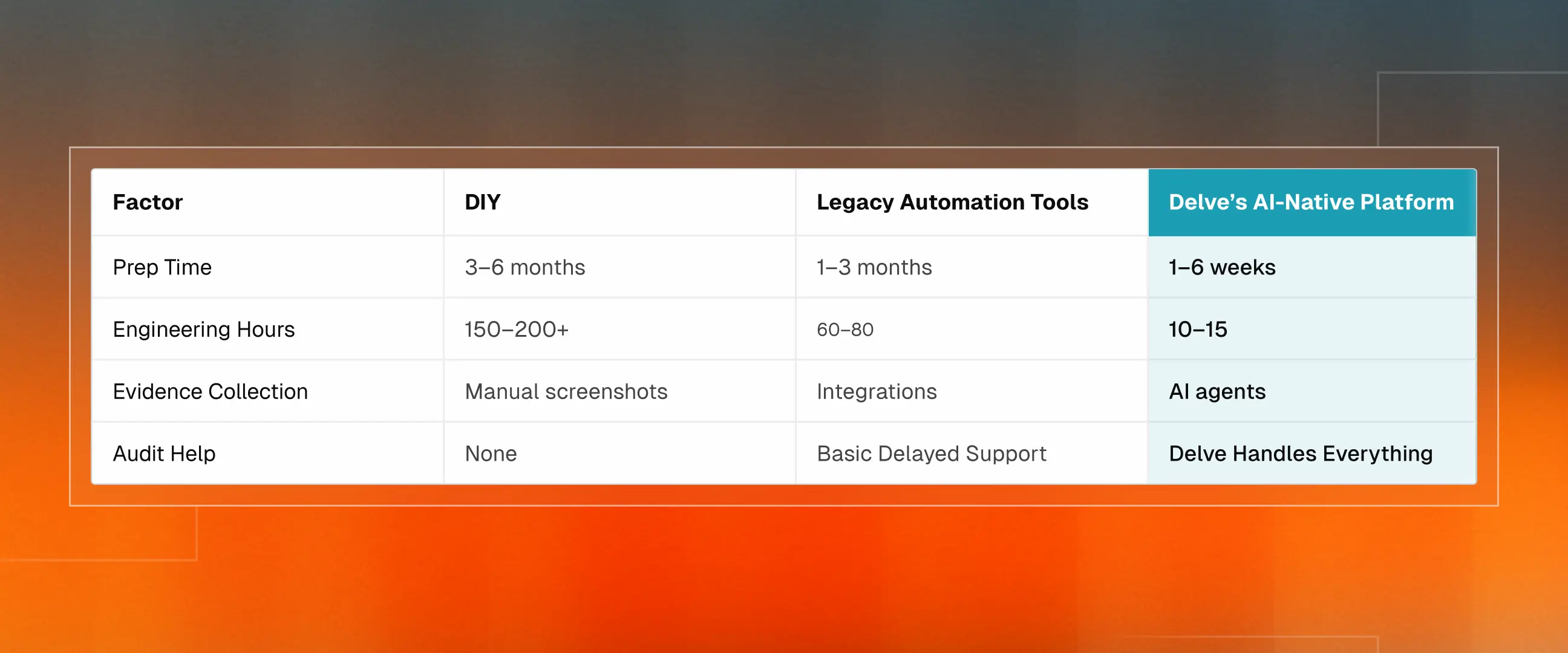
The honest answer depends entirely on how you approach it. We've seen teams get their SOC 2 report in a few days. We've also seen teams drag it out for a year. The difference isn't their tech stack or company size. It's their method. Here's what we typically see:
The Truth Behind Security Automation Claims
Every compliance tool claims to be automated. Here's the reality: most of them automated the easy items. Storing policies, tracking tasks, and running basic checks on your cloud setup. That's helpful, sure. But the burden of complex parts like collecting evidence, figuring out how to fix issues, and dealing with auditors still falls on the engineering team. Teams using such platforms still spend 60-80 hours getting through SOC 2. The "automation" made things a bit easier, but it didn't actually remove the bottleneck.
AI-native platforms like Delve are better suited to the tedious work of logging into systems, taking screenshots, checking configurations, spotting gaps, and more, without your team’s active involvement. When something fails, you get specific guidance for your setup, not generic templates that may or may not apply. Security questionnaires that used to take hours get filled out in minutes with Delve’s AI automation. IBM's 2024 research provides evidence that companies using AI extensively found and contained security issues nearly 100 days faster and spent $2.2 million less when breaches occurred. That's real impact, not marketing.
Don’t Let Compliance Block Any Deal
SOC 2 audit readiness isn't about checking compliance boxes. It's about recovering blocked revenue and removing the tollbooth.
When a $100K enterprise deal stalls in procurement because your startup lacks SOC 2 Type II certification, the conversation shifts from product value to security posture overnight. Enterprise buyers now treat vendor security compliance as a primary purchasing criterion. Gartner projects that 60% of organizations will use security posture as a deal requirement by 2025. For B2B SaaS founders handling customer data in cloud environments,
And the stakes keep getting higher. The IBM Cost of a Data Breach Report 2024 reports an average breach cost of $4.88 million, up 10% from last year. That's the most significant jump since the pandemic began. Enterprise buyers aren't being paranoid. They're being practical. Another Gartner survey found that 45% of companies got burned by third-party security issues in the past two years. No wonder procurement teams are so thorough.
The Founder’s Fast Track to SOC 2 Compliance
SOC 2 audits require a licensed CPA firm to issue your final report. That part is non-negotiable. But most of the work happens before the auditor ever shows up. That's the readiness phase, and it's where founders typically lose months to evidence collection, policy writing, and back-and-forth confusion.
Delve handles this entire readiness phase through its AI-native platform and team, then coordinates directly with trusted CPA audit partners to complete your examination. You never have to manage auditor relationships, chase down evidence, or figure out what's missing. Our Customer Success team owns the communication, timeline, and deliverables, so you can stay focused on building the product.
Delve prevents SOC 2 from becoming an obstacle to your enterprise deals. What separates founders who get compliant in weeks from those who struggle for months isn't complexity. It is the approach.
Don't let manual compliance slow you down.