CMMC Level 1 vs Level 2 vs Level 3

Key Takeaways
- CMMC Level 1 requires 17 basic practices for Federal Contract Information, Level 2 demands 110 controls for Controlled Unclassified Information, and Level 3 adds advanced protections for critical programs, with certification timelines ranging from 4-8 weeks (Level 1) to 12-18 months (Level 3), depending on your starting security posture.
- CMMC certification became mandatory for Defense Industrial Base contractors in 2024, with phased enforcement through 2028, creating urgent timelines. Fewer than 500 organizations have achieved Level 2 certification, even though 80,000+ organizations need it, making early preparation essential before C3PAO bottlenecks worsen.
- Only 4% of defense contractors are truly prepared for CMMC, despite 75% believing they are, creating a significant readiness gap driven by low adoption of essential security controls such as multi-factor authentication, encryption, and incident response capabilities.
- Organizations already compliant with NIST SP 800-171 have a direct path to CMMC Level 2 since all 110 practices map one-to-one. It means existing 800-171 documentation and evidence can accelerate certification by 6-9 months compared to starting from baseline.
- Early certification is quickly becoming a competitive advantage in DoD contract bidding and Delve’s AI-native compliance platforms can compress timelines dramatically through automated evidence collection, continuous posture monitoring, and complete audit handling, reducing manual workload from 200+ hours to 10-15 hours.
The Cybersecurity Maturity Model Certification program represents the Department of Defense's verification framework for contractor cybersecurity. When a procurement team identifies missing CMMC certification as a contract blocker, understanding the level applied and the timeline to achieve it becomes a critical business priority.
The CMMC 2.0 final rule became effective December 16, 2024, consolidating the framework into three certification levels based on information sensitivity. This guide breaks down the requirements, costs, and timelines for each level to help organizations determine their certification pathway.
How Prepared is the Defence Industrial Base Right Now
Recent data reveals a significant gap between perceived and actual compliance across the defense industrial base. According to research by Merrill Research and CyberSheath, only 4% of defense contractors are fully prepared for CMMC certification based on third-party assessment criteria while 75% believe they are compliant based on self-assessment. This 71-percentage-point gap between confidence and reality underscores why the DoD implemented third-party verification requirements.
The CyberSheath 2025 State of the DIB Report found that preparedness actually dropped from 8% in 2023 to 4% in 2024, with only 1% of contractors feeling fully prepared for upcoming assessments. Basic security measure adoption remains limited: only 27% of contractors implement multi-factor authentication, 25% use endpoint detection and response, and 21% deploy vulnerability management tools all of which are requirements under CMMC.
The scale of the challenge is substantial. An estimated 80,000 organizations handle CUI and require Level 2 certification, yet as of October 2025, only 366 firms nationwide hold CMMC Level 2 certification. Meanwhile, 47% of contractors have already received flow-down requests from prime contractors requiring CMMC compliance.
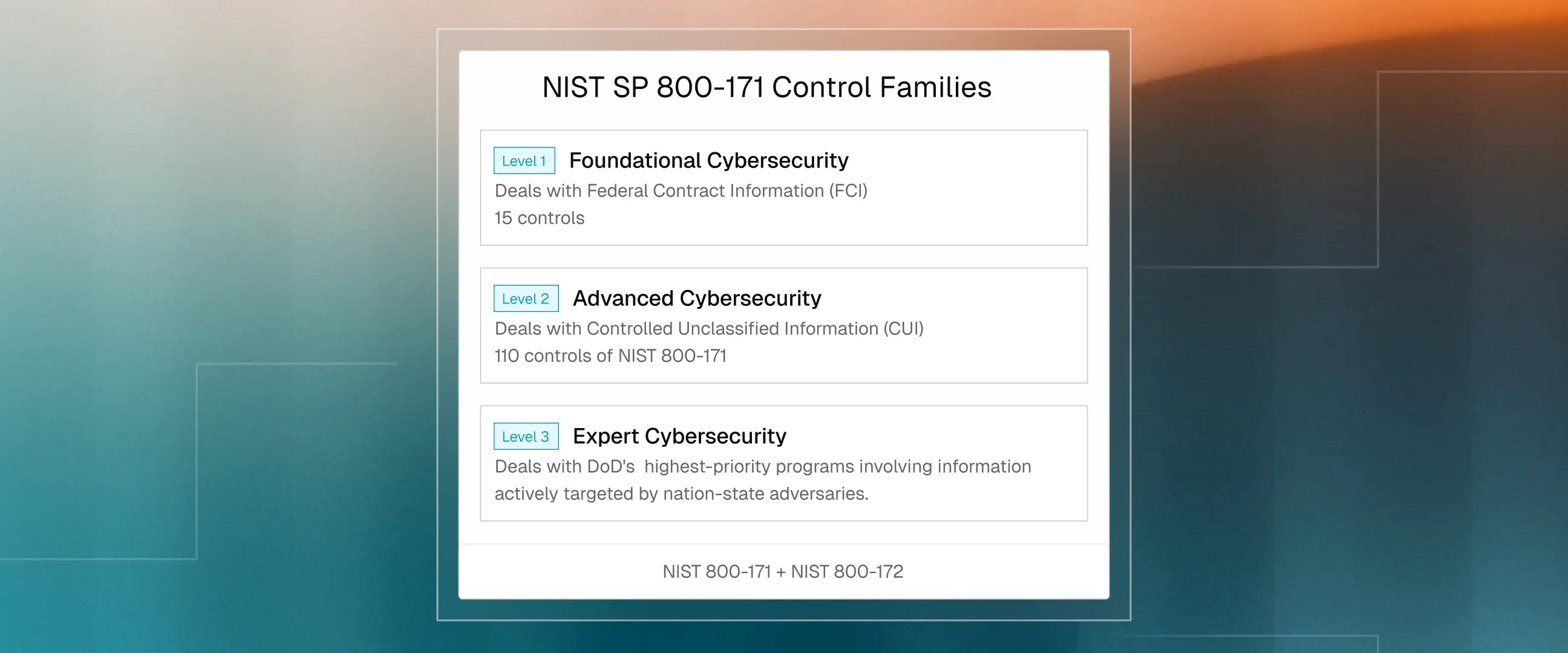
The 3 Levels of CMMC
CMMC Level 1: Foundational Cybersecurity
CMMC Level 1 applies to organizations handling Federal Contract Information (FCI) which includes non-public information generated under government contract such as delivery schedules, correspondence, and pricing. According to DoD estimates, approximately 63% of defense contractors fall into this category.
Level 1 requires implementation of 15 security practices from FAR 52.204-21, covering basic cyber hygiene: access control, identification procedures, media protection, physical security, and system integrity. Assessment consists of annual self-assessment with results submitted to the Supplier Performance Risk System (SPRS), accompanied by a senior official's affirmation.
Cost: The DoD estimates Level 1 self-assessment costs between $4,000 and $6,000 annually, with total implementation and maintenance ranging from $5,000 to $15,000. Organizations with existing IT security practices may already satisfy most Level 1 requirements.
CMMC Level 2: Advanced Cybersecurity for CUI Protection
CMMC Level 2 applies to organizations handling Controlled Unclassified Information (CUI). CUI is the sensitive data requiring protection under law or regulation. The National Archives CUI Registry maintains over 125 CUI categories including technical specifications, engineering drawings, export-controlled data, and source code for defense systems. Any organization touching CUI requires Level 2 certification regardless of volume or frequency.
Level 2 requires implementation of 110 security controls from NIST SP 800-171 Revision 2, organized across 14 control families. Third-party assessment by an authorized C3PAO is required for most CUI-handling contracts, with assessors evaluating compliance against 320 assessment objectives. Organizations scoring at least 88/110 (80%) may receive conditional certification with 180 days to remediate remaining gaps via Plans of Action and Milestones (POA&Ms).
Cost: The DoD projects total Level 2 certification costs at approximately $105,000 for small entities, including C3PAO assessment (~$77,000), planning and preparation (~$21,000), and reporting requirements (~$7,000 over three years). These estimates assume existing NIST 800-171 compliance. Organizations building from baseline face additional remediation costs of $20,000 to $150,000, bringing realistic total budgets to $60,000–$200,000+.
CMMC Level 3: Expert Cybersecurity for Critical Programs
CMMC Level 3 addresses the DoD's highest-priority programs involving information actively targeted by nation-state adversaries. This level applies to critical defense technologies and weapons systems where compromise would significantly harm national security. The DoD designates Level 3 requirements for specific contracts. Organizations requiring this level receive explicit notification.
Level 3 incorporates all 110 NIST SP 800-171 controls plus 24 enhanced requirements from NIST SP 800-172, totaling 134 controls addressing advanced persistent threats. Assessment requires government-led evaluation by the Defense Industrial Base Cybersecurity Assessment Center (DIBCAC), in addition to maintaining valid Level 2 C3PAO certification.
Cost: Government assessment fees approximate $39,000, but preparation for enhanced controls ranges from $100,000 to $500,000+ depending on organizational complexity. Total Level 3 investment typically requires dedicated cybersecurity staff and sophisticated security operations.
Determining Your Required CMMC Level
Contract solicitation language provides the definitive answer. DFARS clause 252.204-7021 specifies the required CMMC level. The presence of DFARS clause 252.204-7012 (Safeguarding Covered Defense Information) indicates CUI handling, which triggers Level 2 requirements.

Implementation Timeline and Deadlines
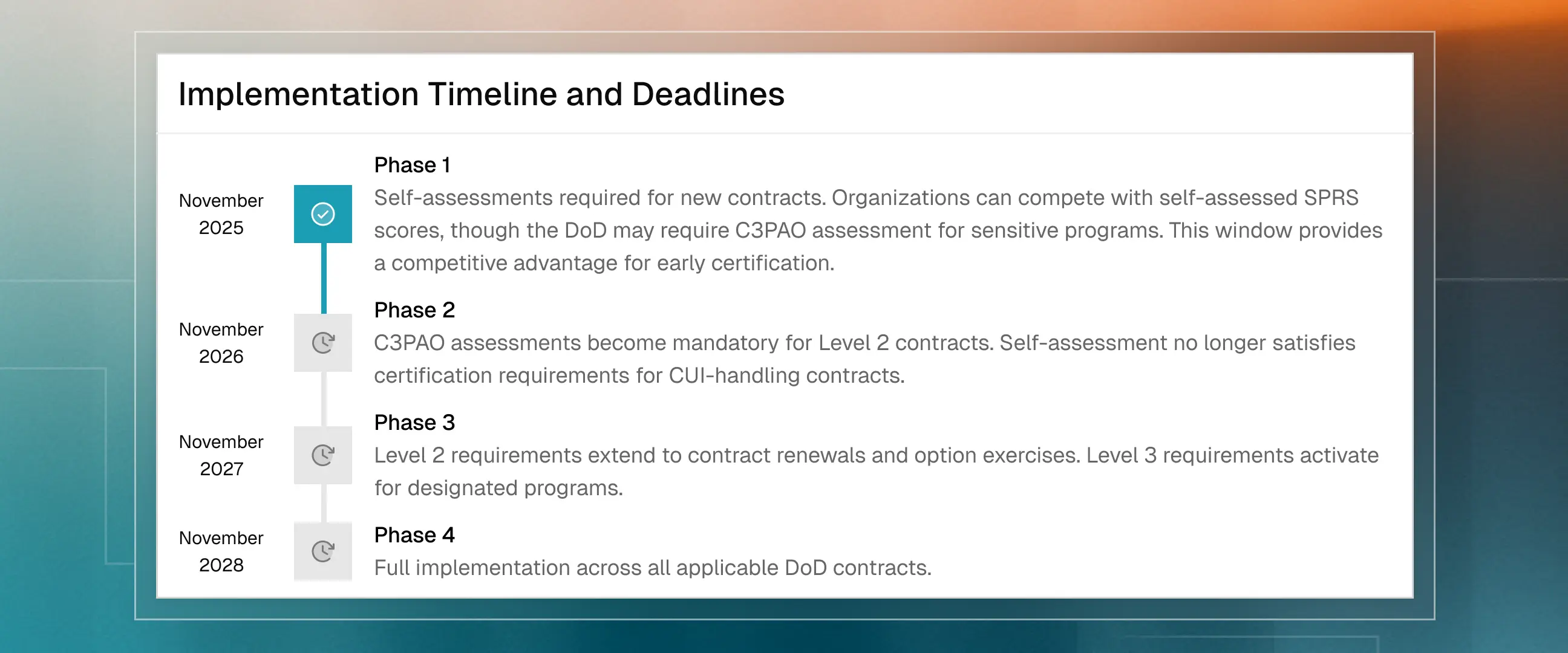
The 48 CFR final rule was published September 10, 2025, with CMMC requirements appearing in contracts starting November 10, 2025. The DoD's phased rollout proceeds as follows:
Phase 1 (November 2025): Self-assessments required for new contracts. Organizations can compete with self-assessed SPRS scores, though the DoD may require C3PAO assessment for sensitive programs. This window provides a competitive advantage for early certification.
Phase 2 (November 2026): C3PAO assessments become mandatory for Level 2 contracts. Self-assessment no longer satisfies certification requirements for CUI-handling contracts.
Phase 3 (November 2027): Level 2 requirements extend to contract renewals and option exercises. Level 3 requirements activate for designated programs.
Phase 4 (November 2028): Full implementation across all applicable DoD contracts.
The practical deadline arrives earlier than these dates suggest. C3PAO lead times currently range from 3 to 6 months, and most organizations require 6 to 12 months of preparation before assessment. There is approximately one assessor organization per 1,000 companies requiring Level 2. With limited C3PAO capacity, scheduling bottlenecks will intensify as mandatory dates approach.
What is the relationship between CMMC and NIST SP 800-171?
CMMC Level 2 directly incorporates NIST SP 800-171. The 110 controls are identical. Organizations that genuinely implemented NIST 800-171 in response to DFARS 252.204-7012 requirements (effective since 2017) have completed the substantive security work for Level 2. The remaining gap is documentation and third-party verification.
However, the data suggests widespread non-compliance with existing requirements. The average SPRS score among surveyed contractors was 12 against a required score of 110 for full compliance. A 2022 CyberSheath study found average scores of -23, indicating minimal improvement over subsequent years.
Organizations with genuine NIST 800-171 implementation typically need 2–4 months of assessment preparation. Those building from baseline require 12–18 months.
What happens if you do not comply?
Contract Eligibility: CMMC status in SPRS serves as a precondition for award. Contracting officers must verify certification before awarding contracts with CMMC requirements.
Existing Contracts: Renewals and option exercises require certification as Phase 3 implementation progresses. Organizations without certification cannot continue contract performance.
Supply Chain Position: Prime contractors bear responsibility for subcontractor compliance. An estimated 70,000 to 75,000 companies handle CUI, but only 1,500 participate in DoD voluntary information-sharing programs. Subcontractors unable to demonstrate CMMC status risk removal from supply chains.
Legal Exposure: Inaccurate SPRS scores or false compliance affirmations create False Claims Act liability. The DoD has emphasized that misrepresenting compliance constitutes fraud.
What problems do founders commonly run into?
Self-Assessment Overconfidence: The 71-point gap between self-assessed compliance (75%) and verified compliance (4%) demonstrates that internal assessments frequently overestimate readiness. Third-party gap assessments provide an accurate baseline measurement.
MSP Dependencies: Organizations delegating IT security to managed service providers must recognize that CMMC assesses the contractor's systems, not the MSP's. Unless providers maintain FedRAMP authorization or independent CMMC certification, contractors must demonstrate compliance through their own implementations.
Timeline Compression: Only 28.7% of organizations have completed a Level 2 assessment with a certified assessor, while 37% remain unscheduled or uncertain about next steps. Organizations that initiate certification efforts after the mandatory assessment dates cannot compress timelines sufficiently.
Delayed Action: The Redspin survey found 13% of contractors had taken no preparatory steps despite years of advance notice. Defense contractors winning business in 2026 and beyond initiated compliance journeys 12–18 months earlier.
Achieve Certification Faster with Delve’s AI-Native Compliance Platform
Delve is built on AI-native automation that goes further by using autonomous browser agents for evidence collection, continuous cloud infrastructure testing, and fully managed C3PAO audit communication through dedicated compliance specialists. The actual workload across organizations using this model drops to 10–15 hours of hands-on effort, compared to the 60–80+ hours required through traditional, manual approaches.
If you're evaluating how to accelerate your certification path, Delve is purpose-built for that. Get in touch with our team now to move quickly and minimize engineering burden.
Don't let manual compliance slow you down.