CMMC Level 2 Requirements Guide

Key Takeaways
- CMMC Level 2 requires meeting 110 federal security rules, passing an independent audit, encrypting all sensitive defense data, using two-factor authentication (MFA) everywhere, hosting data on government-approved cloud services, and achieving at least 88 out of 110 points to be certified.
- CMMC Level 2 is the DoD’s security standard for companies handling CUI, and the 110 required rules are the NIST 800-171 controls across areas like access, encryption, logging, and secure cloud usage.
- To get certified, a DoD-approved C3PAO conducts a formal audit that reviews each of the 110 requirements and your evidence, documentation, and technical controls.
- Engineering teams must cover the key technical pieces: FIPS-validated encryption, MFA everywhere, precise CUI segmentation, logging, vulnerability management, and using FedRAMP Moderate (or IL4+) cloud services where CUI is handled.
- The assessment process is structured: scoping followed by evidence prep then onsite review and SPRS scoring, which leads to conditional/final certification. You must document how your systems work (SSP), show how data flows, and provide artifacts for all 320 assessment objectives.
- The DoD rollout starts in 2025 with selected contracts and expands through 2028, but primes are already pushing subcontractors to meet CMMC early, making “pre-compliance pressure” a real operational requirement today
What is CMMC Level 2 Certification?
CMMC Level 2 is the DoD’s way of ensuring that any company handling Controlled Unclassified Information (CUI) has absolute, verifiable security in place, not just policies on paper. It’s built directly on the 110 controls from NIST SP 800-171 and requires third-party assessments from an accredited C3PAO listed by the CyberAB.
This guide breaks down exactly what CMMC Level 2 requires, how assessments work, and the practical steps to reach certification without derailing engineering velocity.
What CMMC Level 2 Certification Actually Requires
CMMC Level 2 means proving you securely handle defense data (CUI). For that, you:
- Must implement the 110 NIST security controls, use FedRAMP-level cloud + FIPS encryption, and apply MFA everywhere.
- Need clean documentation (SSP, policies, evidence) and a clear CUI boundary.
- Then pass a third-party audit with an SPRS score of 88+ and close minor gaps within 180 days.
What is CUI boundary for CMMC compliance?
A CUI boundary is your blueprint for CMMC. You outline every place CUI lives or moves, and that defines the scope. Do it well, and compliance becomes manageable. Do it sloppy, and everything takes longer, costs more, and risks failing the audit.
The Controls That Actually Matter Most
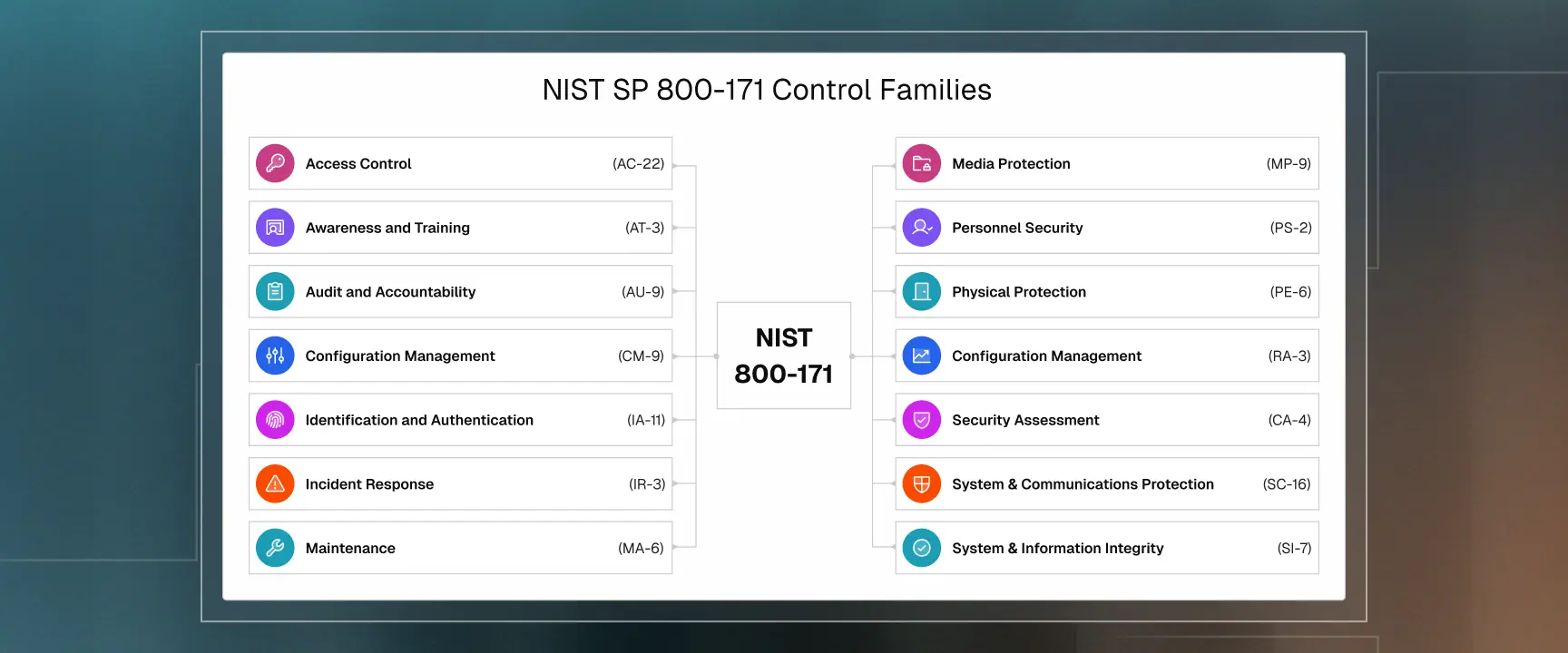
NIST SP 800-171 has 110 controls across 14 families, but not all 110 controls carry equal weight. The DoD CIO's official CMMC program provides authoritative guidance on implementation requirements, and CISA's CMMC 2.0 overview aligns the framework with broader federal cybersecurity standards.
The CMMC scoring methodology assigns point values (1, 3, or 5) based on security impact. You need 88 out of 110 points to pass but certain 5-point controls are non-negotiable and cannot be deferred.
Fail any 5-point control and you cannot achieve certification regardless of your score elsewhere. The complete control specifications are detailed in the CMMC Model Overview document published by DoD CIO.
Apart from controls: Cloud Infrastructure has its own requirements
This is where most startups hit friction. and where imprecise language creates real compliance risk. The DoD Cloud Computing Security Requirements Guide (CC SRG) is explicit: "FedRAMP will serve as the minimum security baseline for all DoD cloud services."
Critical distinction: "FedRAMP-equivalent" is marketing language, not a compliance status. For CUI handling, you need cloud services with actual FedRAMP authorization, verified on the FedRAMP Marketplace—or a DoD Provisional Authorization (PA) at Impact Level 4 or higher.
Compliant options for CUI:
- AWS GovCloud (US): FedRAMP High, DoD IL4/IL5 PA
- Azure Government: FedRAMP High, DoD IL4/IL5 PA
- Google Cloud: FedRAMP High for select services, DoD IL4/IL5 PA for specific offerings
Before selecting any cloud service for CUI, verify its authorization status on the FedRAMP Marketplace or check for DoD PA status. Vague equivalency claims are a red flag that your C3PAO assessor will check.
The enclave approach: Many contractors isolate CUI into a dedicated environment on authorized infrastructure rather than migrating everything. This reduces scope and cost while maintaining compliance.
Encryption must use FIPS 140-2 validated modules and you must verify your provider's certificates on the NIST CMVP validation list.
Understanding C3PAO Certification vs. Self-Assessment
If you handle CUI, the answer is almost always: you need a C3PAO audit.
Self-assessments are only allowed for a small subset of low-risk contracts. For any meaningful DoD work, especially where revenue is on the line, a third-party audit is the expected path.
What does a C3PAO actually do?
They are the independent auditors approved by the Cyber-AB. Their job is to confirm you’ve truly implemented the 110 NIST controls, not just written them on paper.
Is there any scenario where self-assessment is enough?
Only if the DoD explicitly says so in the contract and that’s rare. If you’re handling real CUI or working under a prime contractor, expect a C3PAO audit.
Plan of Action & Milestones (POA&M) Rules
A POA&M is your official list of security gaps that still need to be fixed after the audit. Under 32 CFR § 170.21, only small 1-point issues are allowed on this list. All major 3-point and 5-point controls must already be fully implemented before your assessment. Anything on the POA&M must be closed within 180 days, or your certification expires.
Required Documentation for Assessment
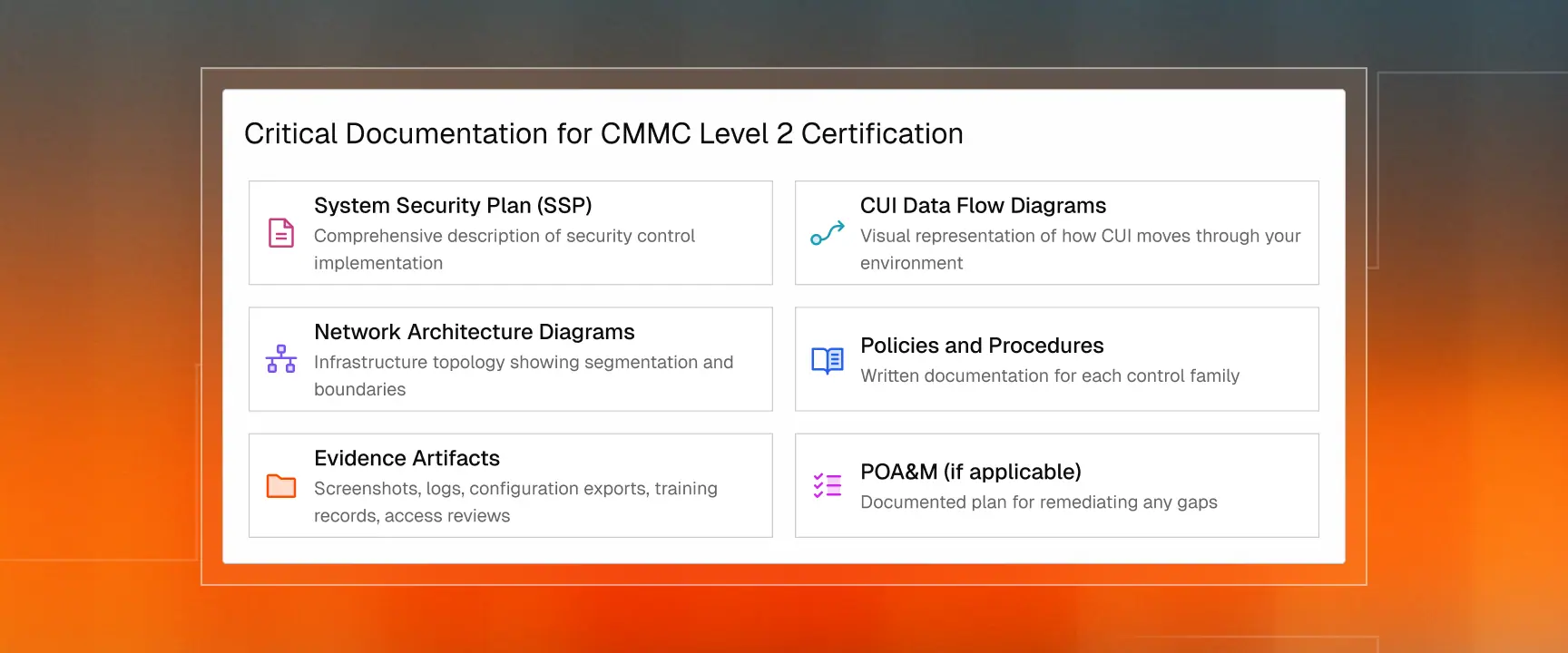
C3PAOs evaluate evidence against each assessment objective. The NIST SP 800-171A assessment procedures provide detailed guidance on evidence requirements for each control.
The Fastest Realistic Path to Certification
The timeline question everyone asks is "How fast can we get this done?" The honest answer depends on your starting point.
If you have existing SOC 2 or ISO 27001 then 4-6 months is realistic. You likely have 40-60% of controls already implemented. Focus on CUI-specific requirements: boundary definition, FIPS encryption, and cloud services with FedRAMP Moderate authorization or DoD IL4+ Provisional Authorization.
If you're starting from scratch then 9-12 months minimum for a small team. You're building the fundamentals of a security program while simultaneously preparing for the assessment.
If you have a deal on the line: Talk to your customer. Many will accept a POA&M or interim letter showing you've started the process and have an assessment scheduled. A Conditional Level 2 status (88+ score with documented remediation plan) is often sufficient for contract award.
What Actually Takes the Time
The bottleneck is usually remediation. Specifically, implementing MFA everywhere, migrating to FedRAMP-authorized cloud services, and deploying FIPS-validated encryption.
The Fastest Path to Certification With Delve
With Delve, contractors move through CMMC Level 2 far faster than traditional consulting or manual workflows. Automated evidence collection replaces months of screenshot hunting. AI-generated policies and SSPs eliminate hundreds of documentation hours. And because Delve manages the entire auditor relationship, your team stays focused on remediation instead of drowning in back-and-forth emails. The result: a compressed, predictable certification timeline driven by automation, not manpower.
While exact timelines vary by environment, customers consistently move much faster with Delve than with traditional consulting or DIY approaches.
If the real bottleneck isn’t cost but time, Delve is built for teams that can’t afford delays. Talk to us to see how we accelerate CMMC timelines without slowing your business down.
How to achieve CMMC Compliance fast?
The hardest part of CMMC isn’t the controls. It’s the timing. Deals don’t wait, and neither do customers. When you’re under pressure, you need speed, not another checklist.
Delve gives you that speed. We automate the boring parts, organize the messy parts, and get you audit-ready fast. If CMMC is slowing your business, Delve helps you move again.
Learn more at our CMMC compliance page.
Don't let manual compliance slow you down.