Get HITRUST-Ready with Delve

Summary
- HITRUST certification requires executive ownership, PHI data mapping, gap assessment against CSF controls, technical remediation (IAM, cloud posture, endpoints), policies written to match actual operations, and validated evidence artifacts, not documentation alone.
- Delve brings AI-native automation and evidence workflows; Com-Sec brings vCISO leadership and healthtech expertise, together delivering a security program, not just a certification
- Most failures occur because teams treat HITRUST as a paperwork project rather than a security program build.
- Technical remediation (IAM, endpoints, cloud posture) takes the longest: plan for weeks 3 to 10.
- Write policies in parallel with building controls to make sure documentation reflects what you actually do.
- Realistic timelines:
- e1: 6–8 weeks
- i1: 8–12 weeks
- r2: 4–9 months (year 2 is materially faster due to interim assessment and rapid recert)
HITRUST readiness usually fails for one reason: most companies treat it as a documentation project rather than a security program build.
Tooling alone won’t get you there. Policies written in isolation won’t get you there. Organizations that pass on the first attempt understand a simple truth: HITRUST requires proof that your security program operates effectively, not just that it’s described on paper.
Healthcare organizations, SaaS companies handling PHI, and businesses pursuing enterprise healthcare contracts face this reality head-on. HITRUST’s rigor is exactly why it carries weight with procurement teams and risk committees—but that rigor also punishes shortcuts. Failed assessments burn months, budget, and stakeholder trust.
Below is the exact, phased process we use with clients to get HITRUST-ready using Delve and Com-Sec vCISO leadership. No theory. Just execution.
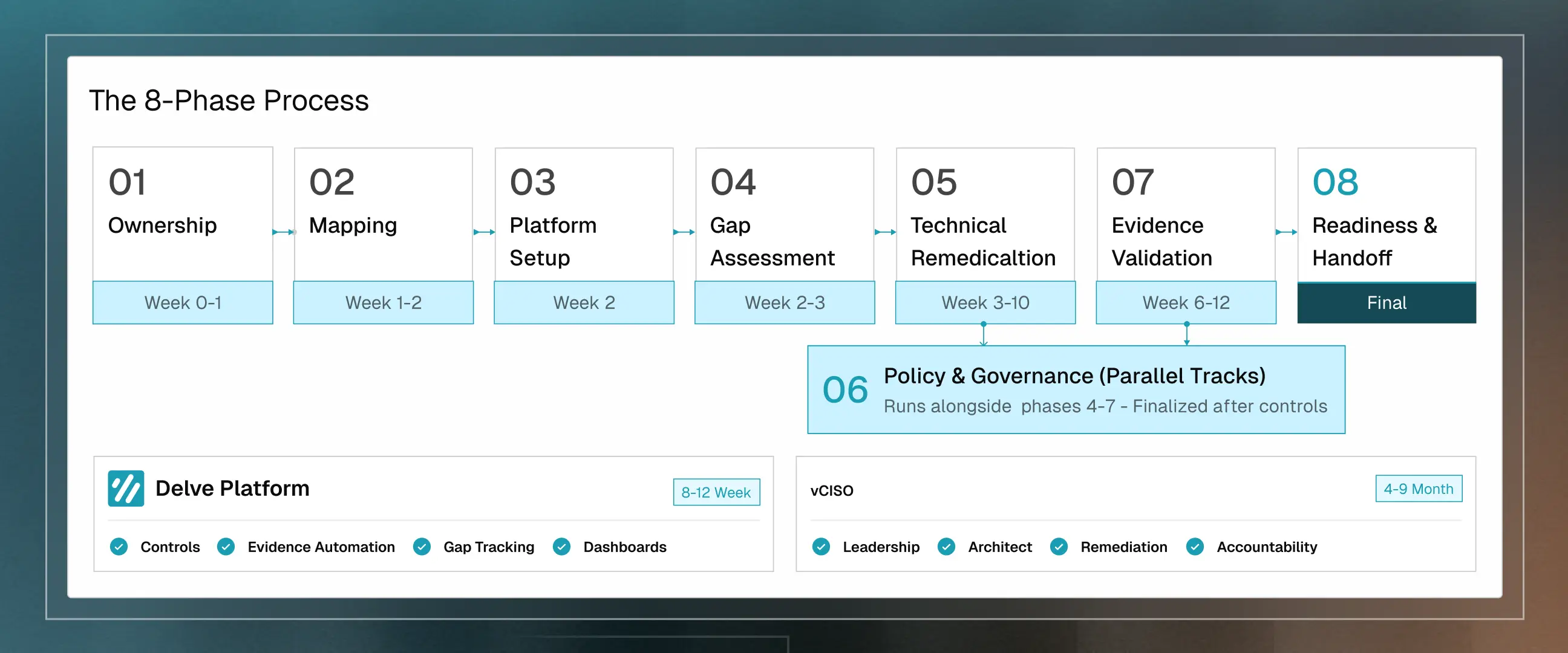
Phase 1: Establish Real Ownership (Week 0-1)
Before any tooling or assessments, you need named owners. HITRUST controls touch infrastructure, HR, vendors, and executive governance. Without clear accountability, remediation stalls and evidence collection turns into chaos. Everyone assumes someone else is handling it until the assessment reveals no one did.
In the first week:
- Assign an internal HITRUST champion and owners executive security owner (vCISO or equivalent)
- Identify technical control owners for cloud, endpoints, applications, and IT
- Lock scope: systems, data flows, vendors, environments
- Define HITRUST assessment type (e1, i1, r2)
- Engage the HITRUST assessor early (align on target dates)
If you skip this, everything downstream breaks. Scope creep and unclear ownership are the two most common reasons HITRUST timelines slip by months. A control without an owner won't get done.
Phase 2: Environment & Data Mapping (Week 1-2)
You can't secure what you haven't mapped. Before implementing any controls, you need complete visibility into where PHI lives, how it moves, and which systems touch it. HITRUST assessors will trace data flows and verify that your controls cover every system in scope. Miss one, and you're scrambling during the assessment.
We:
- Inventorize all in-scope systems (cloud, apps, endpoints, networks)
- Map PHI flows end-to-end
- Identify trust boundaries and integrations
- Classify data under HITRUST control requirements
This mapping serves as the foundation for all control and audit artifacts. It defines your assessment scope and determines which controls apply to your environment. Skip it, and you'll spend remediation chasing systems you didn't know existed.
Phase 3: Delve Platform Setup (Week 2)
Delve becomes the system of record for your HITRUST program. Spreadsheets break at scale: i1 assessments have 40+ controls, r2 can exceed 200. Each needs an owner, evidence artifacts, and maturity validation. Tracking that in Excel leads to version-control nightmares and missed deadlines.
Delve platform handles:
- Policy templates and Control library aligned to HITRUST CSF
- Evidence collection workflows
- Task assignment and tracking
- Maturity scoring
- Auditor-aligned reporting
We:
- Onboard your team and connect your systems to Delve
- Kick off policy and procedure creation using HITRUST-aligned templates (this is a continuous effort until policies are finalized)
- Coordinate with auditors to set up MyCSF platform and submission dates
- Map client systems to controls
- Assign owners at the control level
No spreadsheets. No guessing. Every control has an owner, a status, and a clear path to completion. Real-time dashboards show exactly where you stand and what's blocking progress.
Phase 4: Control Gap Assessment (Week 2-3)
This is where most teams get their first reality check. The gap between the current posture and HITRUST requirements is usually larger than expected.
Even if you've passed SOC 2 or implemented ISO 27001, HITRUST's prescriptive requirements and maturity scoring expose gaps other frameworks don't. The control specificity catches teams off guard: what passed muster elsewhere may fall short here.
For every HITRUST domain, we:
- Validate technical controls: actual configurations, not screenshots
- Validate process controls: operational evidence, not just policies
- Test operational behaviour, not theoretical states
Outputs:
- Control-by-control gap register showing exactly what needs work
- Technical vs administrative gap segmentation for team assignment
- Prioritised remediation plan ranked by risk and effort
The gap assessment determines your remediation timeline. Underestimate it, and you'll miss your assessment window.
Phase 5: Technical Remediation (Weeks 3-10)
This is the heaviest lift. Remediation takes time because it requires fundamental infrastructure changes, not documentation updates. Your engineering team has to implement controls while keeping production systems running. It's a balancing act that demands careful prioritisation.
Typical work includes:
- Endpoint hardening (MDM, EDR, disk encryption)
- IAM cleanup (MFA, RBAC, least privilege)
- Cloud security posture management
- Logging, alerting, SIEM alignment
- Backup, DR, and retention tuning
- Vendor access restrictions
- Secure SDLC and vulnerability management
Delve tracks remediation progress across every control. Com-Sec drives the technical execution. This division of labour keeps engineering focused on fixes while leadership maintains visibility.
Phase 6: Policy & Governance Alignment (Parallel Track)
Policies are finalized after controls exist and are operating, because now they describe reality. Too many organizations write policies before implementing controls, creating documentation that describes aspirational states rather than operational truth.
When your Incident Response policy claims 24-hour containment but you've never tested that capability, assessors notice immediately. Policies written after implementation reflect what your team actually does, not what you hope they'll do someday.
We finalise:
- Information Security Program
- Risk Management
- Access Control
- Vendor Risk
- Data Protection
- Incident Response
- Business Continuity & Disaster Recovery
All mapped directly to implemented controls in Delve.
Phase 7: Evidence Collection & Validation (Weeks 6-12)
HITRUST assessors don't accept claims. They verify artifacts.
Every control requires timestamped proof of operational effectiveness: configuration exports, access logs, vulnerability scan results, and policy acknowledgements. This phase ensures you have documented evidence that controls aren't only implemented but also actively functioning throughout the assessment period.
We:
- Bind live technical evidence to each control in the framework
- Validate operating effectiveness across the whole assessment period
- Run internal readiness checks against HITRUST scoring criteria
- Pre-test auditor expectations through mock reviews
- Identify and close gaps before the assessment day
By this stage, the assessment becomes confirmation, not discovery. Assessors validate what you've already proven internally. No surprises. No scrambling. Just verification of work already done.
Phase 8: Readiness Lock & Assessment Handoff
Before greenlighting the assessment, we verify complete readiness. Going in with open gaps means failed validations, corrective action plans, and timeline extensions. Rushing this decision is the fastest path to audit failure.
Pre-assessment checklist:
- All high-risk controls closed or formally accepted with documented exceptions
- Evidence timestamps aligned to HITRUST testing windows
- Risk exceptions are formally documented and approved by leadership
- Remediation ownership is locked for any remaining open items
Only then do we greenlight the assessment. Moving forward before you're ready creates audit findings, corrective action requirements, and delays that cost more than waiting would have.
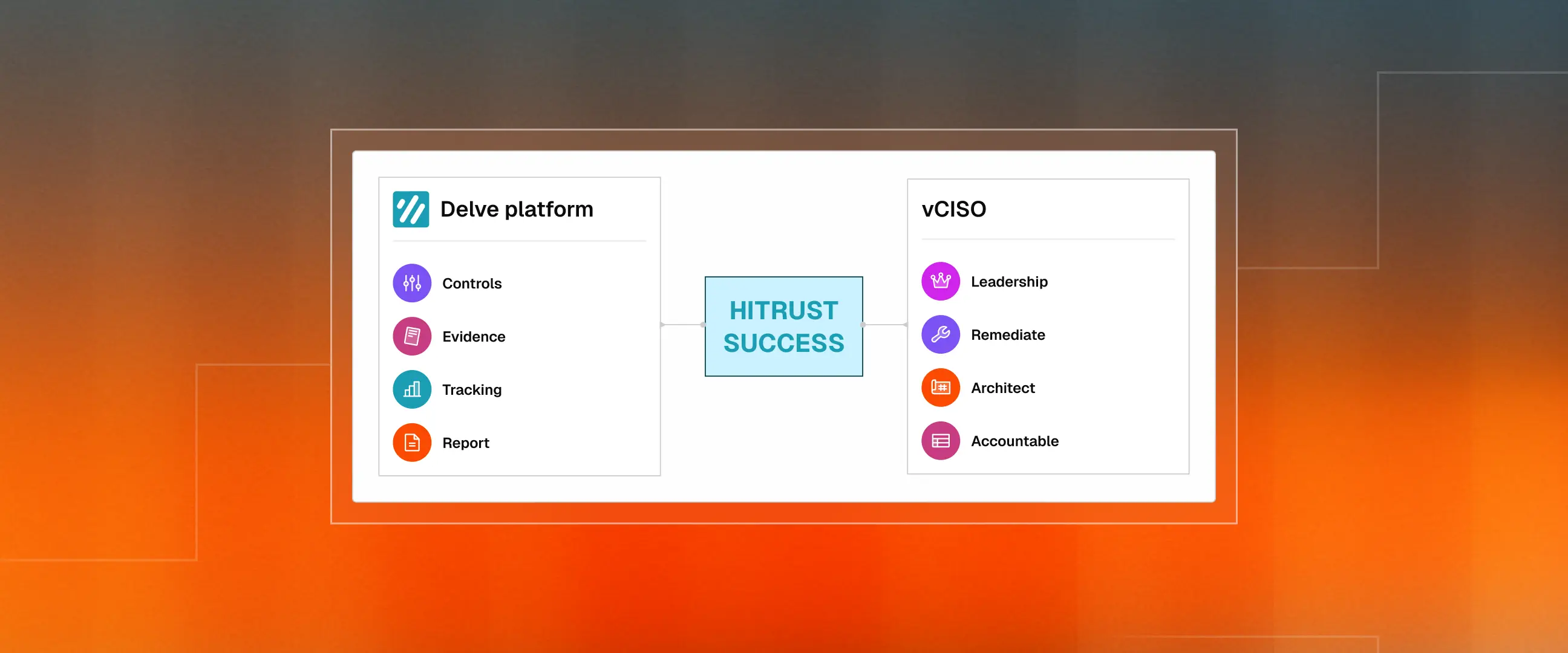
How Delve and Com-Sec Work Together
HITRUST success requires three things: tooling, operational execution, and executive accountability. The platform alone doesn't get you certified and consulting alone doesn't scale as well. You need both working together in harmony. This is how Delve, Com-Sec collaboration creates enormous value for its clients.
Delve handles:
- HITRUST control framework aligned to CSF requirements
- Automated evidence collection workflows
- Gap tracking and remediation management
- Auditor-aligned reporting and readiness dashboards
Com-Sec provides:
- vCISO leadership and program management
- Security architecture design and review
- Technical remediation execution across the infrastructure
- Vendor risk assessment and third-party management
- Cloud and endpoint security implementation
- Incident Response and BC/DR program readiness
- Executive and board-level accountability
Tool + Operator + Executive Ownership. All three are required.
HITRUST Timeline Reality Check
HITRUST timelines depend on assessment type, organizational complexity, and current security maturity. Teams with existing controls move faster. Those starting from scratch need more runway.
Typical timelines:
- e1: 6–8 weeks
- i1: 8 to 12 weeks for organizations with foundational security controls in place
- r2: 4 to 9 months, depending on scope complexity, control count, and remediation requirements
Shortcuts lead to failed validations, not speed. organizations that compress timelines by skipping phases consistently fail initial assessments and spend more time in remediation cycles than they saved. The assessor will find what you missed, so it's better to find it yourself first.
Compliance Without Chaos
HITRUST is not a software problem. It's a security execution problem.
Platforms without operational expertise generate false confidence. Consultants without tooling create unsustainable manual processes. Neither approach delivers certification efficiently.
Delve gives you the platform: control frameworks, evidence automation, and gap tracking. Com-Sec gives you program leadership: vCISO accountability, technical remediation, and security architecture.
If your organization wants HITRUST without chaos (or audit failure), we built this partnership for precisely that. The process works because it treats certification as proof that your security program operates effectively, not evidence that you can fill out forms.
Ready to start? Talk to our team about mapping your path to HITRUST certification with Delve's AI-native compliance platform and Com-Sec's vCISO leadership.
Summary
- HITRUST certification requires executive ownership, PHI data mapping, gap assessment against CSF controls, technical remediation (IAM, cloud posture, endpoints), policies written to match actual operations, and validated evidence artifacts, not documentation alone.
- Delve brings AI-native automation and evidence workflows; Com-Sec brings vCISO leadership and healthtech expertise, together delivering a security program, not just a certification
- Most failures occur because teams treat HITRUST as a paperwork project rather than a security program build.
- Technical remediation (IAM, endpoints, cloud posture) takes the longest: plan for weeks 3 to 10.
- Write policies in parallel with building controls to make sure documentation reflects what you actually do.
- Realistic timelines:
- e1: 6–8 weeks
- i1: 8–12 weeks
- r2: 4–9 months (year 2 is materially faster due to interim assessment and rapid recert)
HITRUST readiness usually fails for one reason: most companies treat it as a documentation project rather than a security program build.
Tooling alone won’t get you there. Policies written in isolation won’t get you there. Organizations that pass on the first attempt understand a simple truth: HITRUST requires proof that your security program operates effectively, not just that it’s described on paper.
Healthcare organizations, SaaS companies handling PHI, and businesses pursuing enterprise healthcare contracts face this reality head-on. HITRUST’s rigor is exactly why it carries weight with procurement teams and risk committees—but that rigor also punishes shortcuts. Failed assessments burn months, budget, and stakeholder trust.
Below is the exact, phased process we use with clients to get HITRUST-ready using Delve and Com-Sec vCISO leadership. No theory. Just execution.

Phase 1: Establish Real Ownership (Week 0-1)
Before any tooling or assessments, you need named owners. HITRUST controls touch infrastructure, HR, vendors, and executive governance. Without clear accountability, remediation stalls and evidence collection turns into chaos. Everyone assumes someone else is handling it until the assessment reveals no one did.
In the first week:
- Assign an internal HITRUST champion and owners executive security owner (vCISO or equivalent)
- Identify technical control owners for cloud, endpoints, applications, and IT
- Lock scope: systems, data flows, vendors, environments
- Define HITRUST assessment type (e1, i1, r2)
- Engage the HITRUST assessor early (align on target dates)
If you skip this, everything downstream breaks. Scope creep and unclear ownership are the two most common reasons HITRUST timelines slip by months. A control without an owner won't get done.
Phase 2: Environment & Data Mapping (Week 1-2)
You can't secure what you haven't mapped. Before implementing any controls, you need complete visibility into where PHI lives, how it moves, and which systems touch it. HITRUST assessors will trace data flows and verify that your controls cover every system in scope. Miss one, and you're scrambling during the assessment.
We:
- Inventorize all in-scope systems (cloud, apps, endpoints, networks)
- Map PHI flows end-to-end
- Identify trust boundaries and integrations
- Classify data under HITRUST control requirements
This mapping serves as the foundation for all control and audit artifacts. It defines your assessment scope and determines which controls apply to your environment. Skip it, and you'll spend remediation chasing systems you didn't know existed.
Phase 3: Delve Platform Setup (Week 2)
Delve becomes the system of record for your HITRUST program. Spreadsheets break at scale: i1 assessments have 40+ controls, r2 can exceed 200. Each needs an owner, evidence artifacts, and maturity validation. Tracking that in Excel leads to version-control nightmares and missed deadlines.
Delve platform handles:
- Policy templates and Control library aligned to HITRUST CSF
- Evidence collection workflows
- Task assignment and tracking
- Maturity scoring
- Auditor-aligned reporting
We:
- Onboard your team and connect your systems to Delve
- Kick off policy and procedure creation using HITRUST-aligned templates (this is a continuous effort until policies are finalized)
- Coordinate with auditors to set up MyCSF platform and submission dates
- Map client systems to controls
- Assign owners at the control level
No spreadsheets. No guessing. Every control has an owner, a status, and a clear path to completion. Real-time dashboards show exactly where you stand and what's blocking progress.
Phase 4: Control Gap Assessment (Week 2-3)
This is where most teams get their first reality check. The gap between the current posture and HITRUST requirements is usually larger than expected.
Even if you've passed SOC 2 or implemented ISO 27001, HITRUST's prescriptive requirements and maturity scoring expose gaps other frameworks don't. The control specificity catches teams off guard: what passed muster elsewhere may fall short here.
For every HITRUST domain, we:
- Validate technical controls: actual configurations, not screenshots
- Validate process controls: operational evidence, not just policies
- Test operational behaviour, not theoretical states
Outputs:
- Control-by-control gap register showing exactly what needs work
- Technical vs administrative gap segmentation for team assignment
- Prioritised remediation plan ranked by risk and effort
The gap assessment determines your remediation timeline. Underestimate it, and you'll miss your assessment window.
Phase 5: Technical Remediation (Weeks 3-10)
This is the heaviest lift. Remediation takes time because it requires fundamental infrastructure changes, not documentation updates. Your engineering team has to implement controls while keeping production systems running. It's a balancing act that demands careful prioritisation.
Typical work includes:
- Endpoint hardening (MDM, EDR, disk encryption)
- IAM cleanup (MFA, RBAC, least privilege)
- Cloud security posture management
- Logging, alerting, SIEM alignment
- Backup, DR, and retention tuning
- Vendor access restrictions
- Secure SDLC and vulnerability management
Delve tracks remediation progress across every control. Com-Sec drives the technical execution. This division of labour keeps engineering focused on fixes while leadership maintains visibility.
Phase 6: Policy & Governance Alignment (Parallel Track)
Policies are finalized after controls exist and are operating, because now they describe reality. Too many organizations write policies before implementing controls, creating documentation that describes aspirational states rather than operational truth.
When your Incident Response policy claims 24-hour containment but you've never tested that capability, assessors notice immediately. Policies written after implementation reflect what your team actually does, not what you hope they'll do someday.
We finalise:
- Information Security Program
- Risk Management
- Access Control
- Vendor Risk
- Data Protection
- Incident Response
- Business Continuity & Disaster Recovery
All mapped directly to implemented controls in Delve.
Phase 7: Evidence Collection & Validation (Weeks 6-12)
HITRUST assessors don't accept claims. They verify artifacts.
Every control requires timestamped proof of operational effectiveness: configuration exports, access logs, vulnerability scan results, and policy acknowledgements. This phase ensures you have documented evidence that controls aren't only implemented but also actively functioning throughout the assessment period.
We:
- Bind live technical evidence to each control in the framework
- Validate operating effectiveness across the whole assessment period
- Run internal readiness checks against HITRUST scoring criteria
- Pre-test auditor expectations through mock reviews
- Identify and close gaps before the assessment day
By this stage, the assessment becomes confirmation, not discovery. Assessors validate what you've already proven internally. No surprises. No scrambling. Just verification of work already done.
Phase 8: Readiness Lock & Assessment Handoff
Before greenlighting the assessment, we verify complete readiness. Going in with open gaps means failed validations, corrective action plans, and timeline extensions. Rushing this decision is the fastest path to audit failure.
Pre-assessment checklist:
- All high-risk controls closed or formally accepted with documented exceptions
- Evidence timestamps aligned to HITRUST testing windows
- Risk exceptions are formally documented and approved by leadership
- Remediation ownership is locked for any remaining open items
Only then do we greenlight the assessment. Moving forward before you're ready creates audit findings, corrective action requirements, and delays that cost more than waiting would have.
How Delve and Com-Sec Work Together
HITRUST success requires three things: tooling, operational execution, and executive accountability. The platform alone doesn't get you certified and consulting alone doesn't scale as well. You need both working together in harmony. This is how Delve, Com-Sec collaboration creates enormous value for its clients.
Delve handles:
- HITRUST control framework aligned to CSF requirements
- Automated evidence collection workflows
- Gap tracking and remediation management
- Auditor-aligned reporting and readiness dashboards
Com-Sec provides:
- vCISO leadership and program management
- Security architecture design and review
- Technical remediation execution across the infrastructure
- Vendor risk assessment and third-party management
- Cloud and endpoint security implementation
- Incident Response and BC/DR program readiness
- Executive and board-level accountability
Tool + Operator + Executive Ownership. All three are required.

HITRUST Timeline Reality Check
HITRUST timelines depend on assessment type, organizational complexity, and current security maturity. Teams with existing controls move faster. Those starting from scratch need more runway.
Typical timelines:
- e1: 6–8 weeks
- i1: 8 to 12 weeks for organizations with foundational security controls in place
- r2: 4 to 9 months, depending on scope complexity, control count, and remediation requirements
Shortcuts lead to failed validations, not speed. organizations that compress timelines by skipping phases consistently fail initial assessments and spend more time in remediation cycles than they saved. The assessor will find what you missed, so it's better to find it yourself first.
Compliance Without Chaos
HITRUST is not a software problem. It's a security execution problem.
Platforms without operational expertise generate false confidence. Consultants without tooling create unsustainable manual processes. Neither approach delivers certification efficiently.
Delve gives you the platform: control frameworks, evidence automation, and gap tracking. Com-Sec gives you program leadership: vCISO accountability, technical remediation, and security architecture.
If your organization wants HITRUST without chaos (or audit failure), we built this partnership for precisely that. The process works because it treats certification as proof that your security program operates effectively, not evidence that you can fill out forms.
21-year-old MIT dropouts raise $32M at $300M valuation led by Insight

Don't let manual compliance slow you down.









.avif)










.webp)

