CMMC Guide For Small Businesses: Costs, Timeline & Requirements

Summary
- CMMC certification for small businesses requires determining your level (1, 2, or 3), scoping your CUI environment, implementing 15-110 controls, and passing a self-assessment or C3PAO audit before contract award.
- DoD's $104,670 estimate excludes implementation costs; realistic first-year spend ranges from $98,000 to $305,000.
- 73% of the Defense Industrial Base is small businesses, yet compliance costs can consume an entire year's profit for contractors with DoD revenue under $500K.
- Enclave strategies can dramatically reduce scope and cost by isolating CUI to a defined boundary.
- Most failures stem from three root causes: evidence gaps, scope creep, and a checkbox mindset
- Timeline reality: 12-18 months from start to certification for focused efforts.
Small businesses pursuing Department of Defense contracts face a compliance cliff. The Cybersecurity Maturity Model Certification program requires defense contractors to prove NIST SP 800-171 implementation through scored assessments before contract award. For the 73% of the Defense Industrial Base that are small businesses, this means navigating 110 security controls, C3PAO assessments, and costs that can exceed $300,000, all while competing with primes that have dedicated compliance teams. This guide breaks down what CMMC actually requires, what it actually costs, and how small contractors can achieve certification without losing the contracts they are trying to win.
CMMC replaces the old ‘Honor System’
Since 2017, defense contractors operated under an honor system. It required contractors to implement NIST SP 800-171 security controls and self-attest to compliance. Contractors submitted scores to the Supplier Performance Risk System (SPRS), but nobody checked whether those scores reflected reality.
CMMC emerged as DoD's response to this systemic failure. It transitions the defense supply chain from what practitioners called a "grade your own test" compliance mode to an assessment-based approach that independently verifies security controls. CMMC requires demonstrable proof through scored assessments, not promises.
The phased rollout began in November 2025. Phase 1 (Self-Assessments) is already initiated. By November 2026, third-party C3PAO assessments become standard for most Level 2 contracts. This guide shares what actually matters for small businesses navigating this transition.
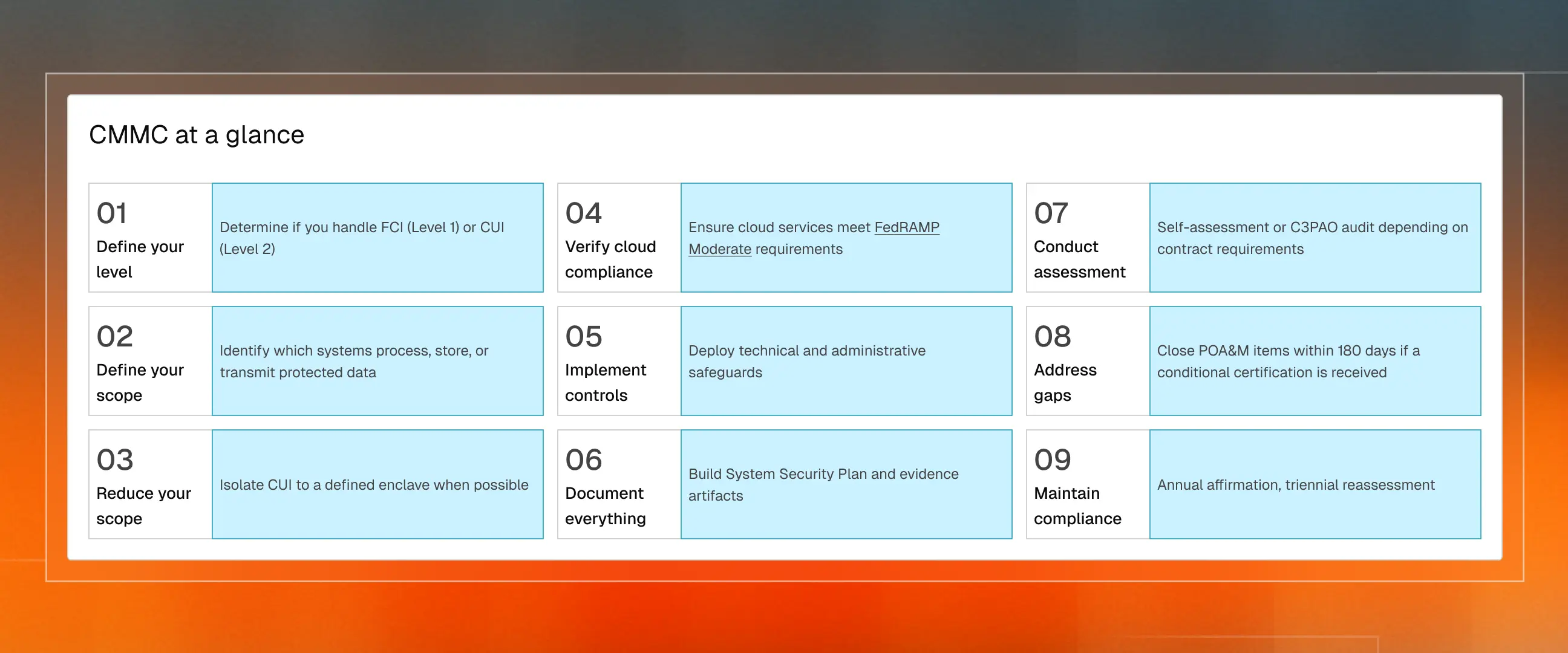
Step 1: Determine which level you need
CMMC has three levels. The level you need depends on the type of data you handle.
- Level 1 (Foundational): This level has 15 basic cybersecurity controls. They come from a federal rule, FAR 52.204-21, and are meant to protect Federal Contract Information (FCI). Level 1 requires an annual self-assessment with results submitted to the Supplier Performance Risk System (SPRS).
Expert Tip: While Level 1 is a self-assessment, it is legally binding. Under the False Claims Act, misrepresenting your security posture in SPRS can lead to severe fines and debarment.
- Level 2 (Advanced): This level has 110 security controls. They are taken from NIST SP 800-171 Rev. 2 and are used to protect Controlled Unclassified Information (CUI). Level 2 requires either self-assessment or third-party C3PAO certification, depending on the criticality of the CUI handled.
- Level 3 (Expert): This level includes all 110 Level 2 controls plus 24 additional controls from NIST SP 800-172. These are used for high-sensitivity government programs requiring enhanced protection against advanced persistent threats. Level 3 requires government-led assessments by DIBCAC. Very few small businesses will need Level 3 certification.
For a deeper comparison, see our complete guide to CMMC Level 1 vs Level 2 vs Level 3.
CMMC levels in a nutshell:
Check your contracts and subcontracts for the mention of any of the following clauses:
- Basic Safeguarding (FAR 52.204-21): It applies when you handle FCI, so Level 1 is required.
- Safeguarding Covered Defense Information (DFARS 252.204-7012): If this clause is present, then you handle CUI, and Level 2 is required.
- CMMC Verification (DFARS 252.204-7021): It applies when the DoD mandates a validated security status, so the specific CMMC level designated in your contract must be met.
Subcontractors should note that if you supply parts, services, or support to a prime contractor with these clauses, flowdown requirements apply. Per 32 CFR 170.23, primes must require subcontractor compliance at all tiers. This is not optional. Large primes are increasingly refusing to work with subcontractors who cannot demonstrate a compliance posture.
Step 2: Learn about the costs of CMMC
The Department of Defense publishes official cost estimates for CMMC certification. You will see the number $104,670 cited everywhere. This number appears in 32 CFR Part 170, gets cited by vendors, and misleads nearly every small business that sees it.
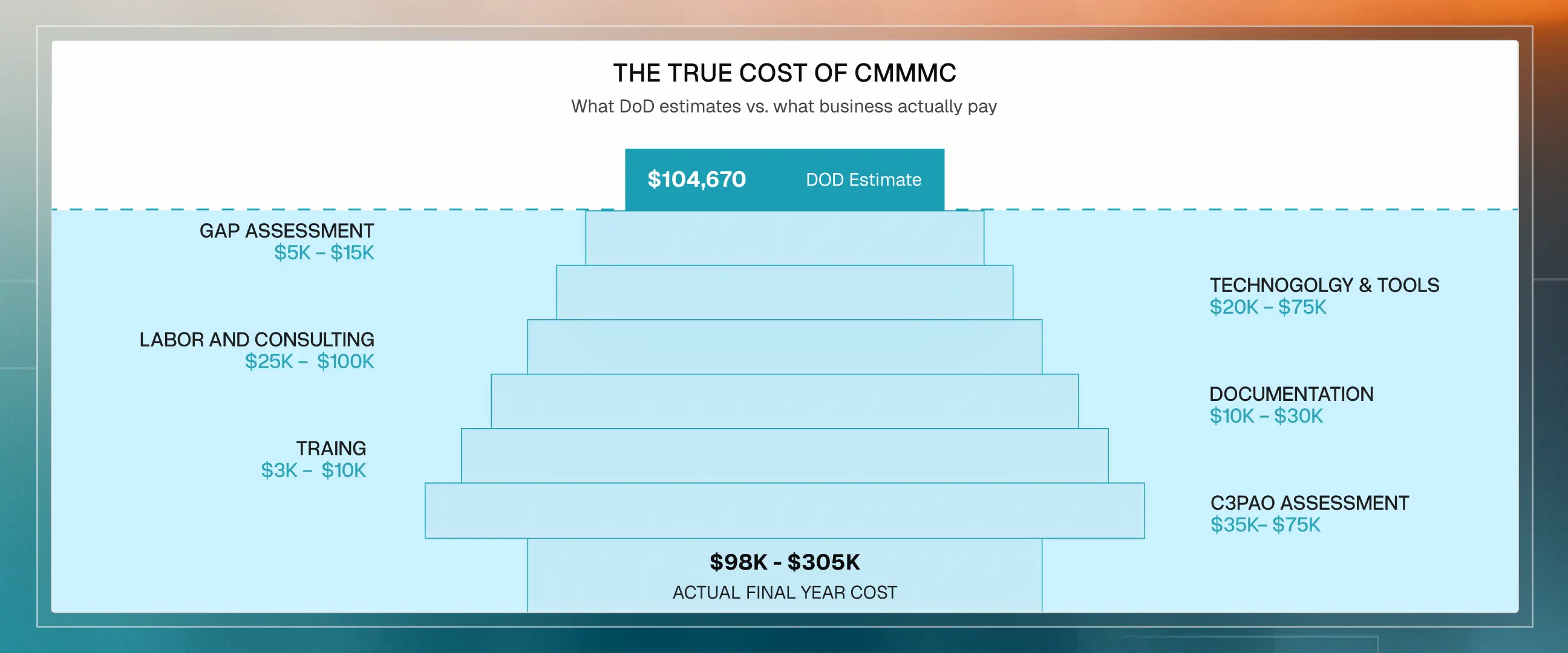
DoD official cost estimates by CMMC level
For Level 2 C3PAO certification, the $104,670 figure covers only assessment, certification, and annual affirmations over three years.
The hidden assumption behind DoD estimates
According to the CMMC Final Rule published in the Federal Register, DoD calculated public costs by considering four categories: nonrecurring engineering costs, recurring engineering costs, assessment costs, and affirmation costs.
For Levels 1 and 2, DoD included only assessment and affirmation costs. DoD assumes you have been compliant with NIST SP 800-171 since 2017. The $104,670 is what you pay to prove compliance. It is not what you pay to achieve it. In DoD's view, implementation costs are expenses you should have incurred years ago. They are not included. For Level 3, they added engineering costs because those security requirements are new. The Federal Register contains a single sentence that explains why every vendor estimate you have seen is wrong:
"DoD did not consider the cost of implementing the security requirements themselves because implementation is already required by FAR clause 52.204-21, effective June 15, 2016, and by DFARS clause 252.204-7012, requiring implementation by Dec. 31, 2017, respectively; therefore, the costs of implementing the security requirements for CMMC Levels 1 and 2 should already have been incurred and are not attributed to this rule."
The problem is that most contractors are not compliant. Industry research consistently shows that fewer than 15% of defense contractors have fully implemented NIST 800-171 controls. If you fall into the other 85%, the DoD estimate has no relationship to your actual costs.
What small businesses actually spend on CMMC
When you include implementation costs, the numbers look completely different. Here is a realistic breakdown for a small business pursuing Level 2 C3PAO certification:
Three-year total cost of ownership
The gap between the DoD estimate and reality ranges from $30,000 to $300,000, depending on your starting security posture.
Step 3: Understand the cost drivers of CMMC
1. Your starting point
Organizations with existing security frameworks like ISO 27001 have a foundation for CMMC. NIST SP 800-171 includes a direct mapping to ISO/IEC 27001 controls. Organizations starting from scratch face significantly higher implementation burdens.
2. How you define scope
CUI touching your entire network means your entire network gets assessed. DFARS 204.75 requires CMMC certification for all information systems that process, store, or transmit CUI. Isolating CUI into a defined enclave shrinks the boundary, the controls, and the price tag.
3. Where the labor comes from
The DoD's CMMC cost estimates explicitly exclude implementation labor because they assume contractors have already incurred those costs under existing DFARS requirements. For organizations starting fresh, internal staff time for policy development, technical implementation, and evidence collection represents the largest line item, and it is where most budgets break.
4. Your starting date
The Cyber AB marketplace lists authorized C3PAOs. With 80,000+ organizations estimated to need Level 2 certification, scheduling assessments early is critical. Waiting means compressed timelines and less flexibility.
Step 4: Does CMMC make financial sense for your small business?
Before committing resources, run the math. If compliance costs approach or exceed your annual DoD revenue, certification may not be viable.
For contractors with thin DoD margins, exiting may be more rational than certifying. For those with strong pipelines, a single new contract can offset the entire investment. But capital is required upfront, before certification unlocks new opportunities. While these numbers are daunting, there is a strategic way to drastically lower them: narrowing your scope through an enclave.
Step 5: Reduce scope and cost via Enclave strategy
The enclave approach helps small businesses save significant money. If only a portion of your organization handles CUI, then you can create a separate, isolated environment for that work. A smaller scope means a simpler assessment, which significantly reduces costs.
Instead of implementing 110 controls across your entire enterprise, you build a dedicated enclave with strict boundaries. CUI stays within that enclave. Your assessment scope shrinks. Your costs follow.
However, this strategy is not right for everyone. An enclave may not be practical if CUI flows through most of your operations. Yet, for many small businesses, it is the difference between affordable compliance and an impossible investment.
Step 6: The Assessment Process: What to Expect
For Level 1, you conduct an annual self-assessment and submit results to SPRS. This is straightforward but must be completed honestly. False attestation carries serious legal consequences under the False Claims Act.
For Level 2 with C3PAO assessment, the process involves several phases:
- Pre-Assessment: Many organizations conduct a readiness review before scheduling the formal assessment. This is where you discover whether you are actually ready. Technical issues like improperly configured encryption or logging mechanisms are often discovered here.
- Formal Assessment: A C3PAO assessor evaluates your implementation of all 110 controls against the 320 assessment objectives. They review documentation, interview personnel across departments, and examine technical implementations. Your score must also reach 80% or higher to qualify for conditional certification. Plan remediation for these controls first.
- POA&M Phase: If gaps are identified, you have 180 days to remediate through a Plan of Action and Milestones. However, not all controls qualify for POA&M treatment, and too many open items signal systemic issues. High-priority 5-point controls, such as External Connections or the System Security Plan itself, must be fully implemented to qualify for even a conditional status.
- Certification: Upon successful completion, your certification is valid for three years with annual affirmations required.
For a step-by-step walkthrough, see our complete CMMC compliance checklist.
Pitfalls that small businesses should avoid
Industry surveys suggest widespread readiness gaps, though official government data on contractor preparedness remains limited. The pattern is consistent: contractors believe they are compliant until an assessor examines their evidence.
The disconnect is predictable. Self-assessment requires no verification. Contractors check boxes, submit scores to SPRS, and assume the work is done. When C3PAO assessors request dated artifacts, access review logs, and training records, the gaps become visible.
This is not a readiness problem. It is a pattern of specific, repeated failures.
Three root causes behind most failures
1. The evidence gap
Contractors implement controls but cannot prove it. Assessors do not evaluate whether you have a policy. They evaluate whether you can demonstrate that policy in action, with dated artifacts, logs, and records. NIST SP 800-171A defines 320 assessment objectives that specify exactly what evidence assessors require.
Common evidence failures occur when:
- Access reviews are conducted but not documented.
- Security training is completed, but no attendance records are retained.
- Incident response plans are written but never tested or exercised.
2. The scope creep trap
Organizations fail to define where CUI lives before starting remediation. When CUI touches everything, everything falls under assessment. 32 CFR 170.19 requires that you define your CMMC Assessment Scope before any assessment. The scope includes all assets that process, store, or transmit CUI.
Scope creep results in ballooning costs, missed deadlines, and controls implemented across systems that should have been excluded. Poor scoping can dramatically inflate costs and extend timelines by months.
3. The checkbox mindset
Contractors treat CMMC like a point-in-time audit rather than a continuous practice. They implement MFA, check the box, and move on. Six months later, an assessor requests evidence of ongoing access reviews and finds none. CMMC requires proof of sustained operation, not a one-time setup.
The controls where these failures concentrate
These five controls share a pattern: they require ongoing evidence, not one-time implementation. Passing means proving continuous practice with documentation that assessors can verify.
For the complete breakdown of all 110 controls and their scoring weights, see our guide to CMMC Level 2 requirements.
Road to CMMC compliance
Most organizations need 12-18 months to achieve full certification. This timeline assumes focused effort. Organizations that treat compliance as a side project or lack dedicated resources often take longer. The earlier you start, the more options you have. Here is a realistic breakdown:
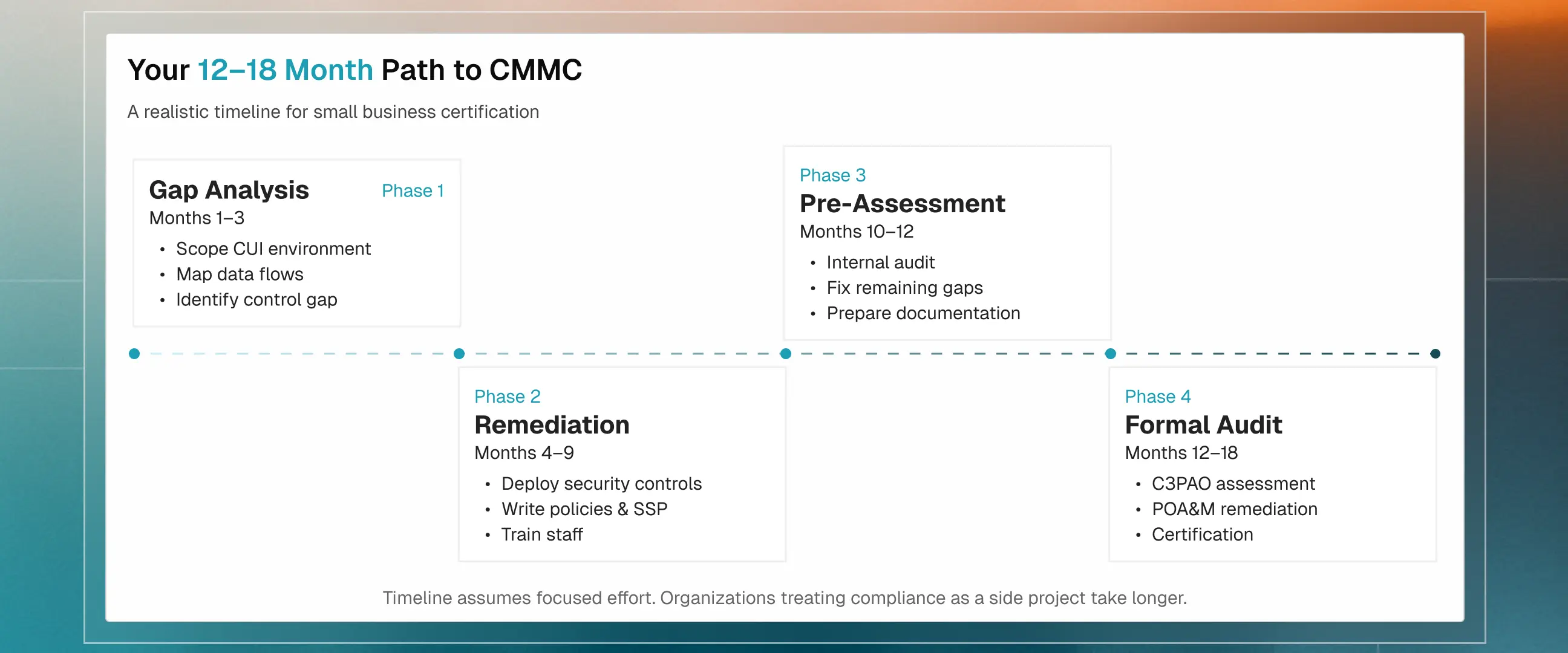
Your path forward: The 3-pillars of success
To navigate the 12 to 18-month journey ahead, keep these three strategies at the forefront of your planning:
- Scope Smart: Don't let your assessment grow unnecessarily; use enclave strategies to isolate CUI and protect your margins.
- Document Early: The "Evidence Gap" is where most failures happen. Start collecting dated artifacts and logs today, not three months before your assessment.
- Move Beyond the Checkbox: Treat NIST 800-171 as a continuous practice rather than a one-time event to ensure you pass your annual affirmations with ease.
How Delve can help
The complexity of CMMC is exactly why we built Delve. We understand that small businesses don't have the luxury of multi-million dollar compliance budgets or massive internal security teams.
Delve helps defense contractors get compliant faster through AI-native automation, continuous monitoring, and managed audit support. Our platform reduces the engineering burden and automates evidence collection, ensuring you are audit-ready and protected against the "Evidence Gap".
Don't wait for the 2026 deadline to find your gaps. Talk to our team today and see how Delve customers are achieving CMMC compliance in weeks, not months.
Don't let manual compliance slow you down.