What is a SOC 2 Report

Key Takeaways
- SOC 2 reports are independent evaluations of a company’s security system based on the AICPA’s Trust Services Criteria
- SOC 2 compliance has become a standard requirement for companies that are pursuing enterprise deals
- There are two SOC 2 report types: Type 1 provides a snapshot of your controls at a single point in time, while Type 2 demonstrates sustained effectiveness over 3 to 12 months
- SOC 2 compliance can help in risk mitigation, closing enterprise deals, and providing companies with a competitive advantage
- AI-native compliance platforms can help businesses be SOC 2-compliant in weeks instead of months
Picture this: you worked hard for months to close an enterprise deal. Everything ran smoothly until procurement asked for security documentation - specifically, your SOC 2 report. It’s no secret that deals often stall when the focus shifts from product value to security concerns. In 2024, IBM’s Cost of a Data Breach Report found that the average cost of a data breach hit a staggering $4.88 million worldwide.
This has led enterprise consumers to push for security verification to be a non-negotiable requirement in their deals. And in recent years, SOC 2 emerged as an integral element in every organization’s security posture. But what exactly is a SOC 2 report?
What is a SOC 2 Report?
A SOC 2 report is a document that proves a service provider’s compliance with standards and policies revolving around data management and security. It was developed by the American Institute of Certified Public Accountants (AICPA) and provided by Certified Public Accountant (CPA) firms. These firms then assess an organization’s security readiness based on the AICPA’s Trust Services Criteria (TSC).
Typically, a SOC 2 report is kept confidential and shared under an NDA with concerned parties during security audits. Organizations must undergo annual security reviews since SOC 2 reports are only valid for 12 months.
What to expect in a SOC 2 report:
There are a number of important sections within every SOC 2 report that enterprise auditors and consumers look into. These are:
- Independent Auditor’s Opinion - the CPA firm’s conclusion on whether or not your organization’s security controls meet the Trust Services Criteria.
- Management Assertion - this is your organization’s attestation of your current security system.
- System Description - a detailed summary of your services, organizational structure, workflows, and infrastructure.
- Trust Services Criteria Mapping - this section illustrates how the security controls in your organization address each of the TSC requirements.
- Controls and Results Tests - a description of the controls that auditors tested, their testing process, and their findings. This section is only included in Type 2 reports.
Type 1 vs. Type 2 Reports
SOC 2 reports come in two different types that serve distinct purposes and differ in time investments.
SOC 2 Type 1 Report in Nutshell:
SOC 2 Type 1 reports are the fastest to obtain of the two report types. They serve as a point-in-time evaluation, meaning an auditing firm checks if your organization’s security system is properly built as of a specific date. This type of report is usually pursued by growing businesses to easily accomplish early-stage due diligence. The downside to Type 1 reports is that they do not attest that security controls will actually work over time. Costs range from $10,000 to $25,000.
SOC 2 Type 2 Report in a Nutshell:
Meanwhile, SOC 2 Type 2 reports determine security readiness over a sustained period that can last anywhere from 3 to 12 months. Auditors evaluate controls within the given time frame. Businesses transition from Type 1 to Type 2 reports when sales cycles are extended, and customer expectations call for sustained compliance. This type of report offers better assurance, therefore being more preferred by enterprise buyers. Costs range from $25,000 to $50,000.
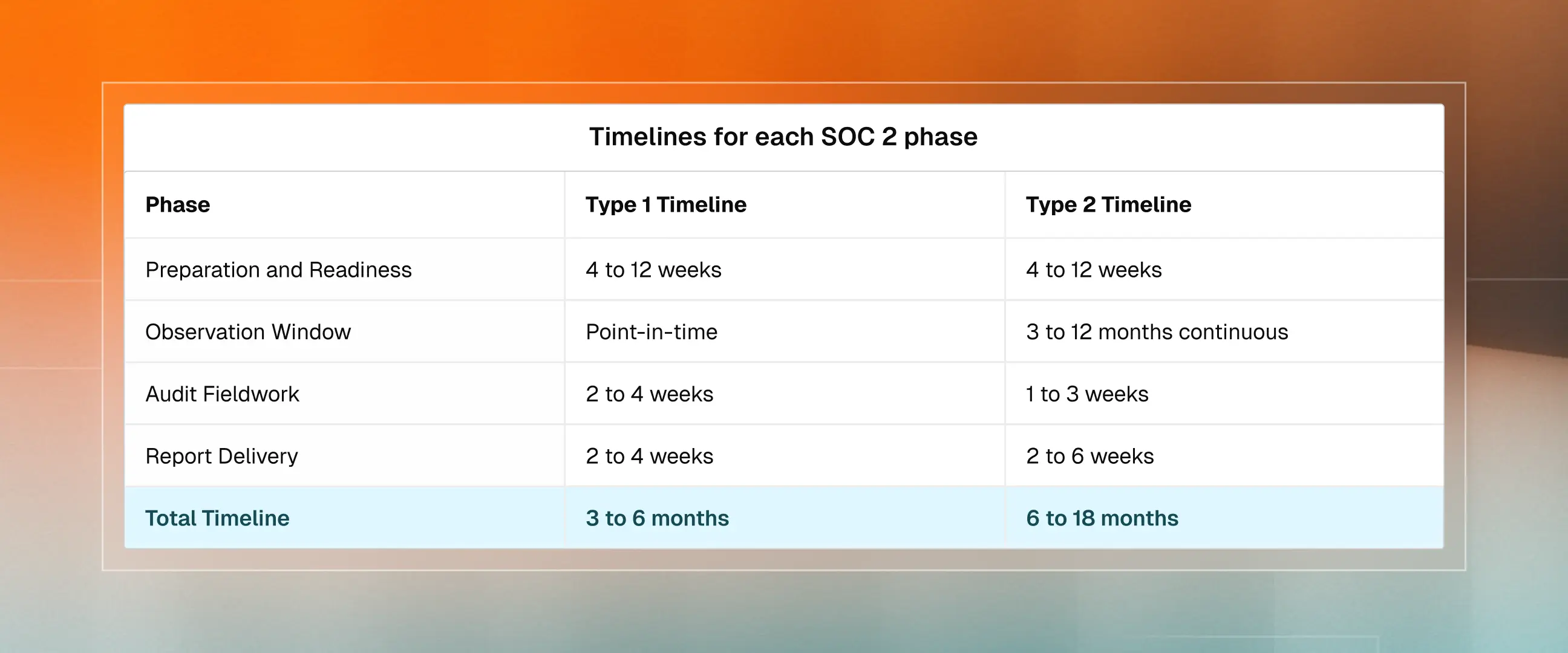
Timelines for each SOC 2 phase:
Understanding the Five Trust Services Criteria
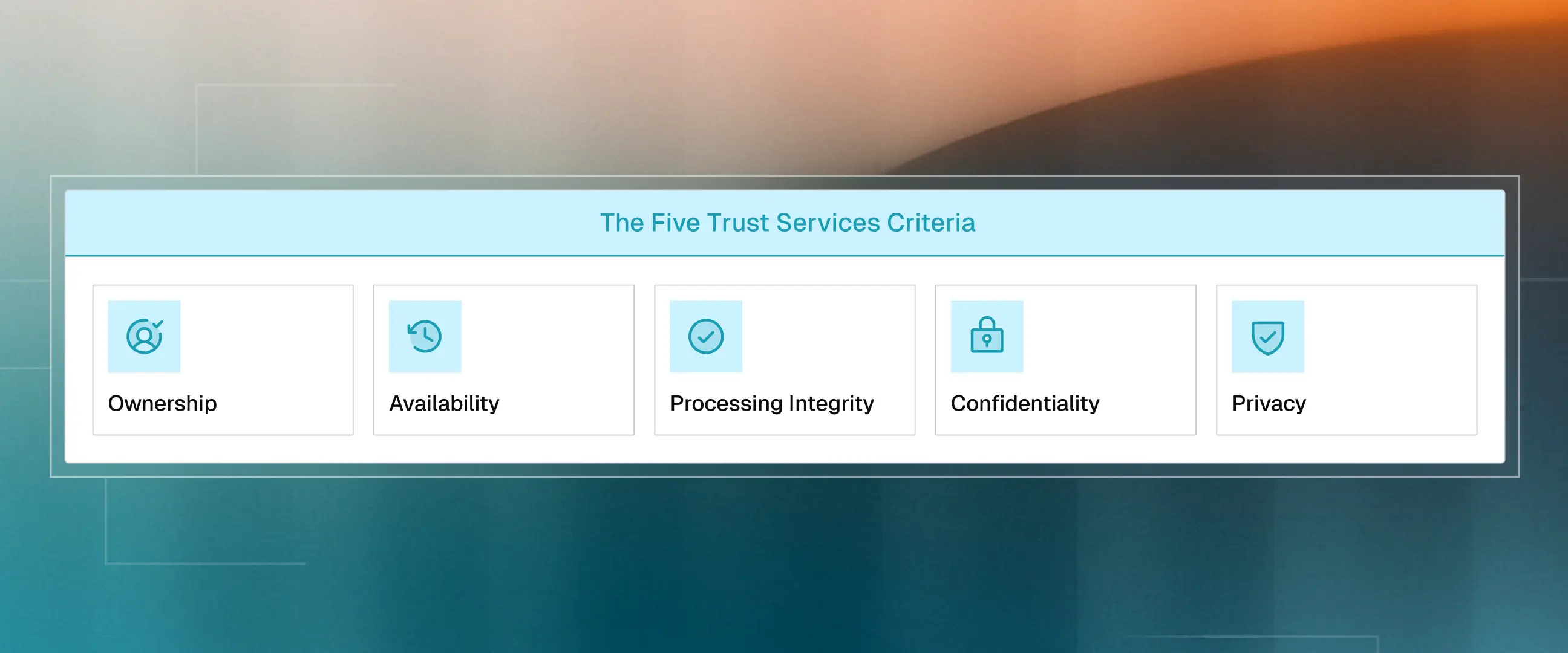
As mentioned earlier, SOC 2 reports are generated based on the five Trust Services Criteria, which examine security, availability, processing integrity, confidentiality, and privacy. In every audit, it is mandatory to review an organization’s security. In contrast, the other four categories are selected according to your business needs.
CBIZ’s 2024 SOC Benchmark Study states that security is assessed in 100% of SOC 2 reports, even though it is not legally required. Followed by availability at 75.3%. Confidentiality’s inclusion spiked from 34% to 64.4% between 2023 and 2024, highlighting the importance of protecting sensitive information as the cost of data breaches increases.
The Five Trust Services Criteria
To know which criteria to look into, you must have a thorough understanding of your target market. Does your company collect and handle personally identifiable information? If so, privacy should be within your scope. If your services offer uptime guarantees via service level agreements, then you should examine availability. Most companies start with security and include other criteria as customer demands evolve.
How to achieve SOC 2 Compliance
To become SOC 2-compliant, your organization needs to take the following steps:
Define Your Scope
In this step, you need to determine which Trust Services Criteria are relevant to your organization. Be sure to also take note of your infrastructure, data flows, and any key information that will be included in your audit.
Identify Gaps
A gap assessment will enhance your SOC 2 audit readiness by giving you a proper idea of your remediation timeline and helping to avoid any unwanted surprises during the audit. This is where you will identify which controls and protocols are in place, and pinpoint the gaps.
Implement Security Controls and Policies
Once you’ve found the gaps in your security system, you can now start addressing them. This can involve several actions, such as setting up multi-factor authentication or re-configuring access controls, implementing security policies, and even organizing employee security awareness training. Having a configuration checklist for SOC 2 compliance can give you an extra advantage in this step if you want to prioritize the elements that auditors are likely to give special attention to.
Gather Evidence
Collect any documentation establishing that your security controls are working properly. Examples of these can be your organization’s access logs, system configurations, policy acknowledgments, training completion records, and many more. You may opt to leverage AI-driven documentation tools that automate record-keeping by taking screenshots from integrated systems such as GitHub, AWS, and other HR tools.
Work with an Auditor
Now that you have the crucial documentation, you can enlist the help of a licensed CPA firm that has proven experience working with technology companies. Walk them through the key information necessary for them to perform their audit, like your scope, SOC 2 audit timeline, and the type of report your organization needs. From there, the auditor will study your documentation, conduct personnel interviews, and test your system.
Complete the Audit and Maintain Compliance
It is vital that you are able to address auditor requests immediately during the audit if you wish to adhere to your established timelines. The auditor’s report should be shared with concerned parties via a secure trust center as soon as you receive it. It’s worth noting that SOC 2 compliance is not a one-time deal and requires ongoing oversight, annual reviews, and system updates as your business needs grow.
The importance of SOC 2 Reports
SOC 2 certification has a direct impact on business growth and revenue. It is tied to your company’s credibility as it serves as proof of trustworthiness. This type of data security compliance brings the following benefits:
- Competitive Advantage - SOC 2 compliance can set your company apart from competitors in crowded markets because it demonstrates your commitment to protecting your customers. This is especially helpful when engaging with clients from industries where security expectations are significantly high, like digital payments, healthcare, and SaaS.
- Enterprise Deals - Organizations with SOC 2 reports tend to close enterprise deals faster since they meet security requirements from the get-go. And enterprise buyers have now turned vendor security verification into a mandatory step in conducting their business deals. What makes SOC 2 reports powerful is this: they can answer security questionnaires with a single document, therefore eliminating the need for constant back-and-forth between you and your potential customers.
- Risk Mitigation - We know just how costly data breaches can be. With SOC 2 compliance, businesses are compelled to implement rigid risk management protocols such as real-time risk detection, continuous monitoring, and incident reporting. Thus, avoiding any operational disruptions like those that affected over 70% of breached organizations in 2024, as reported by IBM.
Industries that need SOC 2 compliance
Most companies that handle critical data should be SOC 2-compliant. This framework applies to:
- SaaS and cloud service providers
- Healthcare technology services that collect patient information
- Fintech companies that process transactions
- Data analytics firms that manage client data
SOC 2 compliance is often required by enterprise clients contractually, even though it is not legally mandatory. This is because SOC 2 reports have become the industry standard proof of security readiness. Many large-scale businesses refuse to make deals with vendors that lack a SOC 2 report.
Get SOC 2-compliant with Delve
SOC 2 compliance shouldn’t keep you from landing your next enterprise deal.
With Delve’s AI-native compliance platform, businesses can streamline the compliance process without sacrificing quality. Documentation is collected directly from your systems; no need for manual screenshots! Our dedicated Customer Success team will engage with auditors, which will save your team over 40+ hours of communications. And our real-time readiness feedback will inform you exactly when you’re up for audit.
Book a demo and be SOC 2-compliant with Delve.
Key Takeaways
- SOC 2 reports are independent evaluations of a company’s security system based on the AICPA’s Trust Services Criteria
- SOC 2 compliance has become a standard requirement for companies that are pursuing enterprise deals
- There are two SOC 2 report types: Type 1 provides a snapshot of your controls at a single point in time, while Type 2 demonstrates sustained effectiveness over 3 to 12 months
- SOC 2 compliance can help in risk mitigation, closing enterprise deals, and providing companies with a competitive advantage
- AI-native compliance platforms can help businesses be SOC 2-compliant in weeks instead of months
Picture this: you worked hard for months to close an enterprise deal. Everything ran smoothly until procurement asked for security documentation - specifically, your SOC 2 report. It’s no secret that deals often stall when the focus shifts from product value to security concerns. In 2024, IBM’s Cost of a Data Breach Report found that the average cost of a data breach hit a staggering $4.88 million worldwide.
This has led enterprise consumers to push for security verification to be a non-negotiable requirement in their deals. And in recent years, SOC 2 emerged as an integral element in every organization’s security posture. But what exactly is a SOC 2 report?
What is a SOC 2 Report?
A SOC 2 report is a document that proves a service provider’s compliance with standards and policies revolving around data management and security. It was developed by the American Institute of Certified Public Accountants (AICPA) and provided by Certified Public Accountant (CPA) firms. These firms then assess an organization’s security readiness based on the AICPA’s Trust Services Criteria (TSC).
Typically, a SOC 2 report is kept confidential and shared under an NDA with concerned parties during security audits. Organizations must undergo annual security reviews since SOC 2 reports are only valid for 12 months.
What to expect in a SOC 2 report:
There are a number of important sections within every SOC 2 report that enterprise auditors and consumers look into. These are:
- Independent Auditor’s Opinion - the CPA firm’s conclusion on whether or not your organization’s security controls meet the Trust Services Criteria.
- Management Assertion - this is your organization’s attestation of your current security system.
- System Description - a detailed summary of your services, organizational structure, workflows, and infrastructure.
- Trust Services Criteria Mapping - this section illustrates how the security controls in your organization address each of the TSC requirements.
- Controls and Results Tests - a description of the controls that auditors tested, their testing process, and their findings. This section is only included in Type 2 reports.
Type 1 vs. Type 2 Reports
SOC 2 reports come in two different types that serve distinct purposes and differ in time investments.
SOC 2 Type 1 Report in Nutshell:
SOC 2 Type 1 reports are the fastest to obtain of the two report types. They serve as a point-in-time evaluation, meaning an auditing firm checks if your organization’s security system is properly built as of a specific date. This type of report is usually pursued by growing businesses to easily accomplish early-stage due diligence. The downside to Type 1 reports is that they do not attest that security controls will actually work over time. Costs range from $10,000 to $25,000.
SOC 2 Type 2 Report in a Nutshell:
Meanwhile, SOC 2 Type 2 reports determine security readiness over a sustained period that can last anywhere from 3 to 12 months. Auditors evaluate controls within the given time frame. Businesses transition from Type 1 to Type 2 reports when sales cycles are extended, and customer expectations call for sustained compliance. This type of report offers better assurance, therefore being more preferred by enterprise buyers. Costs range from $25,000 to $50,000.
Timelines for each SOC 2 phase:

Understanding the Five Trust Services Criteria

As mentioned earlier, SOC 2 reports are generated based on the five Trust Services Criteria, which examine security, availability, processing integrity, confidentiality, and privacy. In every audit, it is mandatory to review an organization’s security. In contrast, the other four categories are selected according to your business needs.
CBIZ’s 2024 SOC Benchmark Study states that security is assessed in 100% of SOC 2 reports, even though it is not legally required. Followed by availability at 75.3%. Confidentiality’s inclusion spiked from 34% to 64.4% between 2023 and 2024, highlighting the importance of protecting sensitive information as the cost of data breaches increases.
The Five Trust Services Criteria
To know which criteria to look into, you must have a thorough understanding of your target market. Does your company collect and handle personally identifiable information? If so, privacy should be within your scope. If your services offer uptime guarantees via service level agreements, then you should examine availability. Most companies start with security and include other criteria as customer demands evolve.
How to achieve SOC 2 Compliance
To become SOC 2-compliant, your organization needs to take the following steps:
Define Your Scope
In this step, you need to determine which Trust Services Criteria are relevant to your organization. Be sure to also take note of your infrastructure, data flows, and any key information that will be included in your audit.
Identify Gaps
A gap assessment will enhance your SOC 2 audit readiness by giving you a proper idea of your remediation timeline and helping to avoid any unwanted surprises during the audit. This is where you will identify which controls and protocols are in place, and pinpoint the gaps.
Implement Security Controls and Policies
Once you’ve found the gaps in your security system, you can now start addressing them. This can involve several actions, such as setting up multi-factor authentication or re-configuring access controls, implementing security policies, and even organizing employee security awareness training. Having a configuration checklist for SOC 2 compliance can give you an extra advantage in this step if you want to prioritize the elements that auditors are likely to give special attention to.
Gather Evidence
Collect any documentation establishing that your security controls are working properly. Examples of these can be your organization’s access logs, system configurations, policy acknowledgments, training completion records, and many more. You may opt to leverage AI-driven documentation tools that automate record-keeping by taking screenshots from integrated systems such as GitHub, AWS, and other HR tools.
Work with an Auditor
Now that you have the crucial documentation, you can enlist the help of a licensed CPA firm that has proven experience working with technology companies. Walk them through the key information necessary for them to perform their audit, like your scope, SOC 2 audit timeline, and the type of report your organization needs. From there, the auditor will study your documentation, conduct personnel interviews, and test your system.
Complete the Audit and Maintain Compliance
It is vital that you are able to address auditor requests immediately during the audit if you wish to adhere to your established timelines. The auditor’s report should be shared with concerned parties via a secure trust center as soon as you receive it. It’s worth noting that SOC 2 compliance is not a one-time deal and requires ongoing oversight, annual reviews, and system updates as your business needs grow.
The importance of SOC 2 Reports
SOC 2 certification has a direct impact on business growth and revenue. It is tied to your company’s credibility as it serves as proof of trustworthiness. This type of data security compliance brings the following benefits:
- Competitive Advantage - SOC 2 compliance can set your company apart from competitors in crowded markets because it demonstrates your commitment to protecting your customers. This is especially helpful when engaging with clients from industries where security expectations are significantly high, like digital payments, healthcare, and SaaS.
- Enterprise Deals - Organizations with SOC 2 reports tend to close enterprise deals faster since they meet security requirements from the get-go. And enterprise buyers have now turned vendor security verification into a mandatory step in conducting their business deals. What makes SOC 2 reports powerful is this: they can answer security questionnaires with a single document, therefore eliminating the need for constant back-and-forth between you and your potential customers.
- Risk Mitigation - We know just how costly data breaches can be. With SOC 2 compliance, businesses are compelled to implement rigid risk management protocols such as real-time risk detection, continuous monitoring, and incident reporting. Thus, avoiding any operational disruptions like those that affected over 70% of breached organizations in 2024, as reported by IBM.
Industries that need SOC 2 compliance
Most companies that handle critical data should be SOC 2-compliant. This framework applies to:
- SaaS and cloud service providers
- Healthcare technology services that collect patient information
- Fintech companies that process transactions
- Data analytics firms that manage client data
SOC 2 compliance is often required by enterprise clients contractually, even though it is not legally mandatory. This is because SOC 2 reports have become the industry standard proof of security readiness. Many large-scale businesses refuse to make deals with vendors that lack a SOC 2 report.
Get SOC 2-compliant with Delve
SOC 2 compliance shouldn’t keep you from landing your next enterprise deal.
With Delve’s AI-native compliance platform, businesses can streamline the compliance process without sacrificing quality. Documentation is collected directly from your systems; no need for manual screenshots! Our dedicated Customer Success team will engage with auditors, which will save your team over 40+ hours of communications. And our real-time readiness feedback will inform you exactly when you’re up for audit.
21-year-old MIT dropouts raise $32M at $300M valuation led by Insight

Don't let manual compliance slow you down.







.avif)










.webp)

